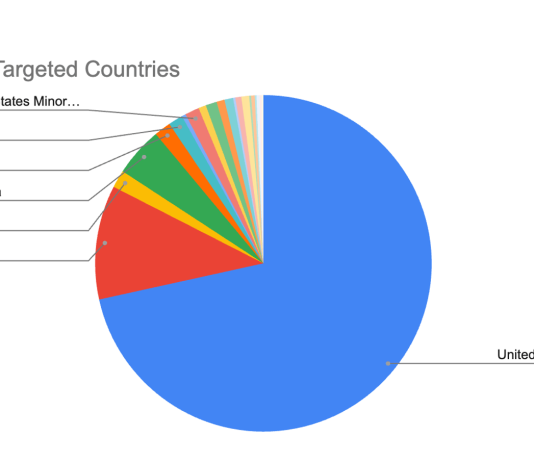
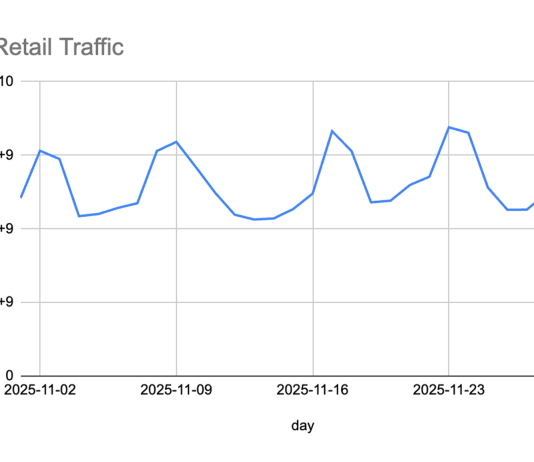
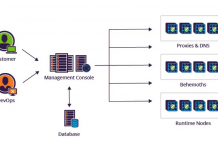
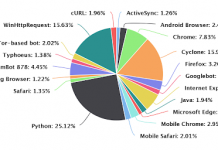
44% of Security Professionals Spend More than 20 Hours a Week Responding to Alerts
As the global cybersecurity climate continues to heat up, so too do the subsequent levels of alert fatigue IT security professionals have to deal...
Survey: 44% of Security Professionals Spend More than 20 Hours a Week Responding to...
As the global cybersecurity climate continues to heat up, so too do the subsequent levels of alert fatigue IT security professionals have to deal...
Read: How To Build Resilient Cloud Configuration Shields
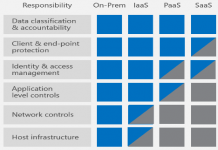
Configurable systems have a high level of flexibility and are better adapted to most customer needs, but their management isn’t a trivial task in...
The World’s Most Popular Coding Language Happens to be Most Hackers’ Weapon of Choice
Python will soon be the world’s most prevalent coding language.
That’s quite a statement, but if you look at its simplicity, flexibility and the...
Imperva Joins Global Cybersecurity Tech Accord
Imperva is dedicated to the global fight to keep people’s data and applications safe from cybercriminals. What this means for our Imperva Threat Research...
Microsoft and Imperva Collaboration Bolsters Data Compliance and Security Capabilities
This article explains how Imperva SecureSphere V13.2 has leveraged the latest Microsoft EventHub enhancements to help customers maintain compliance and security controls as regulated...
Explainer Series: RDaaS Security and Managing Compliance Through Database Audit and Monitoring Controls
As organizations move to cloud database platforms they shouldn’t forget that data security and compliance requirements remain an obligation. This article explains how you...
Taking Stock: The Internet of Things, and Machine Learning Algorithms at War
It’s in the news every day; hackers targeting banks, hospitals, or, as we’ve come to fear the most, elections.
Suffice to say then that cybersecurity...
Imperva Recognized as a 2018 Gartner Magic Quadrant WAF Leader, Five Years Running
Gartner has named Imperva as a Leader in the 2018 Gartner Magic Quadrant for Web Application Firewalls (WAF) — for the fifth year in...
Report: Nearly Half of Security Professionals Think They Could Execute a Successful Insider Attack...
As potential threats and entry points into organizations’ databases keep growing, so does the amount of money folks are throwing at detecting and actioning...