It’s Time for Managers to Lead Security by Example, Not Blame Younger Workers
The age gap is something that all organisations over the years have had to deal with in one way or another. But the flood...
What kids get up to online
Today’s children navigate the Internet better than adults. They are not afraid to try out new technology, and are quick to grasp new trends...
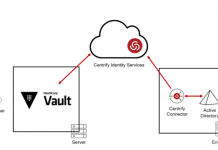
Introducing Centrify Identity Services for HashiCorp Vault
Today, Centrify is proud to announce the integration of the Centrify Identity Service with HashiCorp Vault for role-based user authentication and access to the...
A MitM extension for Chrome
Browser extensions make our lives easier: they hide obtrusive advertising, translate text, help us choose in online stores, etc. There are also less desirable...
Gaza Cybergang Group1, operation SneakyPastes
Gaza Cybergang(s) is a politically motivated Arabic-language cyberthreat actor, actively targeting the MENA (Middle East North Africa) region, especially the Palestinian Territories.
The confusion surrounding...
Still Stealing
Two years ago in October 2015 we published a blogpost about a popular malware that was being distributed from the Google Play Store. Over...
Goodfellas, the Brazilian carding scene is after you
There are three ways of doing things in the malware business: the right way, the wrong way and the way Brazilians do it. From...
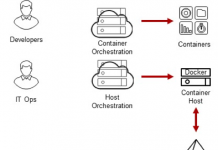
Centrify Identity Services: Securing Docker and Containers
Introduction
We are excited to announce that Centrify now supports CoreOS Container Optimized Linux which several of our customers are using as part of their...
How to Authenticate Users Into Apps Using AWS Application Load Balancer and Centrify
At Centrify, an AWS Partner Network (APN) Advanced Technology Partner, we frequently work with developers building applications on Amazon Web Services (AWS). While many aspects of app...
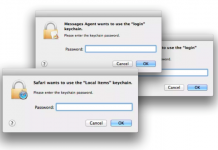
Sync Your Jaws Into Mac Keychain
“Well this is not a boat accident! It wasn’t any propeller! It wasn’t any coral reef! And it wasn’t Jack the Ripper! It was...