Trending Now
Featured news
What do Equifax, HBO, Uber and Yahoo All Have in Common?
A consumer ratings agency, a cable network, a transportation company and a web services provider. What ties them together? Sure, they were all impacted...
Tech News
Tech
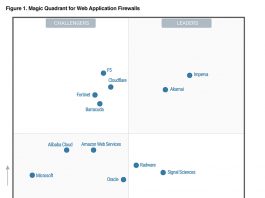
The Gartner CISO Playbook: Leveraging Effective Control in the Cloud
For as long as we can remember, the concept of control has rested comfortably in physical location and ownership. It’s simple, if you could...
Security
Five Critical Steps of a Complete Security Risk and Compliance Lifecycle
Five Critical Steps of a Complete Security Risk and Compliance Lifecycle #outlook...
Closing the Integrity Gap with NIST’s Cybersecurity Framework
Closing the Integrity Gap with NIST's Cybersecurity Framework #outlook a{ padding:0; }...
Women in Tech and Career Spotlight: Jerusalem Bicha
We conclude our series featuring women in tech at Imperva with an interview with Jerusalem Bicha, network operations team lead at Imperva. We talked...
Building a Mature Vulnerability Management Program
Building a Mature Vulnerability Management Program #outlook a{ padding:0; } body{ width:100%...
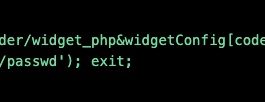
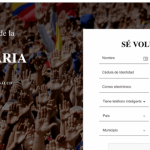
DNS Manipulation in Venezuela in regards to the Humanitarian Aid Campaign
Venezuela is a country facing an uncertain moment in its history. Reports suggests it is in significant need of humanitarian aid.
On February 10th, Mr....