Python will soon be the world’s most prevalent coding language.
That’s quite a statement, but if you look at its simplicity, flexibility and the relative ease with which folks pick it up, it’s not hard to see why The Economist recently touted it as the soon-to-be most used language, globally. Naturally, our threat research team had to poke around and see how popular Python is among bad actors.
And the best place to do that, well, Github, of course. Roughly estimating, more than 20% of GitHub repositories that implement an attack tool / exploit PoC are written in Python. In virtually every security-related topic in GitHub, the majority of the repositories are written in Python, including tools such as w3af , Sqlmap, and even the infamous AutoSploit tool.
At Imperva, we use an advanced intelligent Client Classification mechanism that distinguishes and classifies various web clients. When we take a look at our data, specifically security incidents, the majority of the clients (>25%) we identify — excluding vulnerability scanners — are based on Python.
Unlike other clients, in Python, we see a host of different attack vectors and the usage of known exploits. Hackers, like developers, enjoy Python’s advantages which makes it a popular hacking tool.

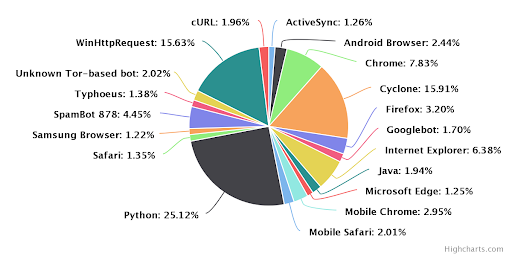
Figure 1: Security incidents by client, excluding vulnerability scanners. More than 25% of the clients were Python-based tools used by malicious actors, making it the most common vector for launching exploit attempts.
When examining the use of Python in attacks against sites we protect, the result was unsurprising – a large chunk, up to 77%, of the sites were attacked by a Python-based tool, and in over a third of the cases a Python-based tool was responsible for the majority of daily attacks. These levels, over time, show that Python-based tools are used for both breadth and depth scanning.

Figure 2: Daily percentage of sites suffering Python-based attacks
Python Modules
The two most popular Python modules used for web attacks are Urllib and Python Requests. The chart below shows attack distribution. Use of the new module, Async IO, is just kicking off, which makes perfect sense when you consider the vast possibilities the library offers in the field of layer 7 DDoS; especially when using a “Spray N’ Pray” technique:

Python and Known Exploits
The advantages of Python as a coding language make it a popular tool for implementing known exploits. We collected information on the top 10 vulnerabilities recently used by a Python-based tool, and we don’t expect it to stop.
The two most popular attacks in the last 2 months used CVE-2017-9841 – a PHP based Remote Code Execution (RCE) vulnerability in the PHPUnit framework, and CVE-2015-8562 which is a RCE against the Joomla! Framework. It isn’t surprising that the most common attacks had RCE potential, considering how valuable it is to malicious actors.
Another example, which isn’t in the top 10, is CVE-2018-1000207, which had hundreds of attacks each day for several days during the last week of August 2018. Deeper analysis shows that the attack was carried out on multiple protected customers, by a group of IPs from China.
CVEs over time

You can see that the number of CVEs which are being used by attackers, according to our data, has increased in the last few years:

In addition, Python is used to target specific applications and frameworks – below you can find the top 10, according to our data:

When we looked at all the frameworks targeted by Python, the attacks that stand out are those aimed at Struts, WordPress, Joomla and Drupal, which is not surprising as these are currently some of the most popular frameworks out there.
Attack vectors
The most popular HTTP parameter value we’ve seen used in attacks, responsible for around 30% of all different param values used, belongs to a backdoor upload attempt through a PHP Unserialize vulnerability in Joomla! using the JDatabaseDriverMysqli object. The backdoor uploaded payload is hosted on ICG-AuthExploiterBot.
We’ve also seen a recurring payload that turned out to be a Coinbitminer infection attempt, more details on that are in the appendix — note, the appendix is only meant as an example. Since Python is so widely used by hackers, there is a host of different attack vectors to take into consideration. Python requires minimal coding skills, making it easy to write a script and exploit a vulnerability.
Our recommendation
Unless you can differentiate between requests from Python-based tools and any other tool, our recommendations stay the same – make sure to keep security in mind when developing, keep your system up to date with patches, and refrain from any practice that is considered insecure.
Appendix – Example of an Attack
Here’s an interesting, recurring payload we’ve observed (with a small variance at the end):

After base64 decoding it, we get a binary payload:

In the above payload, there is a mention of a GitHub repository for a deserialization exploitation tool and a wget command download in a jpg file, which strongly suggests there is malicious activity. After downloading the file from http://45.227.252.250/jre.jpg we can see that it’s actually a script containing the following:

The two last lines in the script try to get http://45.227.252.250/static/font.jpg%7Csh, which is identified as Trojan. Coinbitminer by Symantec Endpoint Protection.

This finding relates to a tweet from the end of August 2018, talking about a new Apache Struts vulnerability CVE-2018-11776 used to infect with the same Coinbitminer.
While you’re here, also read: Imperva Python SDK – We’re All Consenting SecOps Here