Dark Tequila Añejo
Dark Tequila is a complex malicious campaign targeting Mexican users, with the primary purpose of stealing financial information, as well as login credentials to...
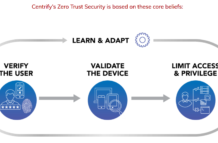
Minimizing Exposure to Ransomware Attacks with Centrify Zero Trust Privilege
Ransomware attacks like the ones that wreaked havoc in Baltimore, Maryland, Albany, New York, and Genesee County, Michigan are dominating the headlines in 2019....
GUEST BLOG: A Gen Z’s Perspective on Cybersecurity
I had the pleasure to mentor a summer intern named Min Ji Kim, who is returning to NYU to continue her education next week....
Centrify for NIST 800-171 MFA Compliance
I often speak with Federal System Integrators (FSIs) who need to implement Multi-Factor Authentication (MFA) as part of their NIST 800-171 compliance.
Specifically section 3.5.3...
Getting started with WAPIs using POSTMAN
Read more
IoT lottery: finding a perfectly secure connected device
Black Friday and Cyber Monday are great for shopping. Vendors flood the market with all kinds of goods, including lots of exciting connected devices...
How to Attack and Defend a Prosthetic Arm
The IoT world has long since grown beyond the now-ubiquitous smartwatches, smartphones, smart coffee machines, cars capable of sending tweets and Facebook posts and...
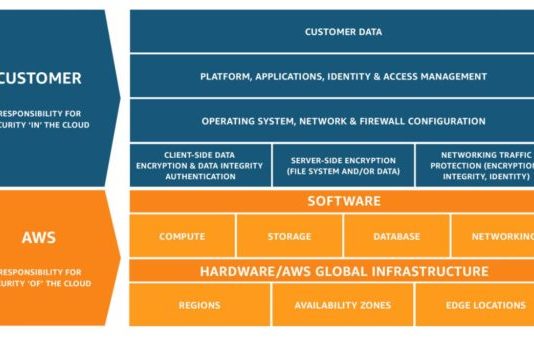
Smart Cloud Security
Learn More
DG and Netskope for enterprise DLP + cloud access security
1
- Read more