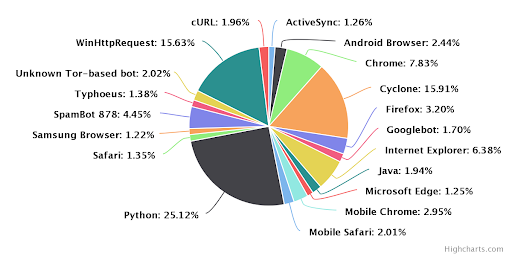
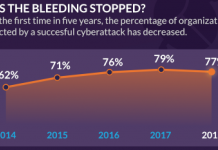
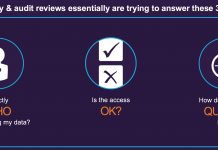
2018 Cyberthreat Defense Report: Where IT Security Is Going
What keeps you awake at night? We asked IT security professionals the same question and found that these issues are top of mind: malware...
NEW: Vulnerability and Assessment Scanning for Your AWS Cloud Databases
Scuba is a free and easy-to-use tool that uncovers hidden security risks. Scuba is frequently updated with content from Imperva’s Defense Center researchers.
With Scuba...
Read: New Attack Analytics Dashboard Streamlines Security Investigations
Attack Analytics, launched this May, aimed to crush the maddening pace of alerts that security teams were receiving. For security analysts unable to triage...
2017 OWASP Top 10: The Good, the Bad and the Ugly
Since its founding in 2001, the Open Web Application Security Project (OWASP) has become a leading resource for online security best practices. In particular,...
Now-Patched Google Photos Vulnerability Let Hackers Track Your Friends and Location History
A now-patched vulnerability in the web version of Google Photos allowed malicious websites to expose where, when, and with whom your photos were taken.
Background
One...
A Quick-Start Introduction to Database Security: An Operational Approach
The recent SingHealth data breach incident exposed around 1.5 million patients’ records. In its aftermath, the Cyber Security Agency of Singapore published a set...
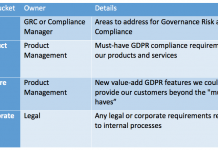
One GRC Manager’s Practical Approach to GDPR Readiness
With about four months to go before the GDPR becomes effective many companies are still struggling with where to start. You’re not alone. According...
The Data Breach ‘Kill Chain’: Early Detection is Key
Today, organizations rely heavily on data, with a big portion of that data made up of sensitive information. As organizations become the custodians of...
Imperva Cloud WAF and Graylog, Part II: How to Collect and Ingest SIEM Logs
This guide gives step-by-step guidance on how to collect and parse Imperva Cloud Web Application Firewall (WAF, formerly Incapsula) logs into the Graylog SIEM...
Imperva Python SDK – We’re All Consenting SecOps Here
Managing your WAF can be a complicated task. Custom policies, signatures, application profiles, gateway plugins… there’s a good reason ours is considered the best...