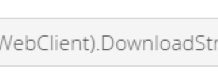
A Deep Dive into Database Attacks [Part III]: Why Scarlett Johansson’s Picture Got My...
As part of Imperva’s efforts to protect our customers’ data, we have an ongoing research project focused on analyzing and sharing different attack methods...
Cloud Migration Fundamentals
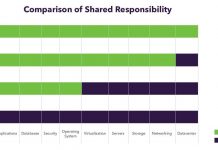
The advantages offered by a cloud-based environment make it an easy decision for most companies to make. Still, there are numerous critical choices to...
Seven Must-Dos to Secure MySQL 8.0
Most database breaches are blamed on insiders such as employees who are either malicious or whose security has been compromised. In fact, most of...
Back to Basics: Let’s Forget About the GDPR… For A Moment
At this point it’s fairly safe to assume that most everyone in the business of “data” has heard of the European Union (EU)-wide General...
Hunting for Insider Threats: Using Activity Modeling to Detect Suspicious Database Commands and Access...
The Widening Gap
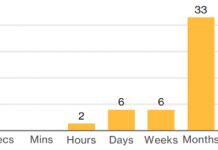
Data breaches by insiders are very challenging to catch. The gap between the rise of insider threats and speed of hunting them...
Read: How To Build Resilient Cloud Configuration Shields
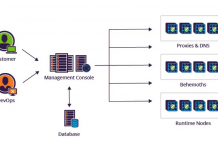
Configurable systems have a high level of flexibility and are better adapted to most customer needs, but their management isn’t a trivial task in...
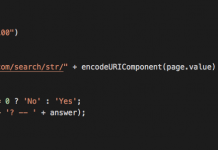
A Deep Dive into Database Attacks [Part IV]: Delivery and Execution of Malicious Executables...
In a previous post we covered different techniques for execution of SQL and OS commands through Microsoft SQL server that can be used for...
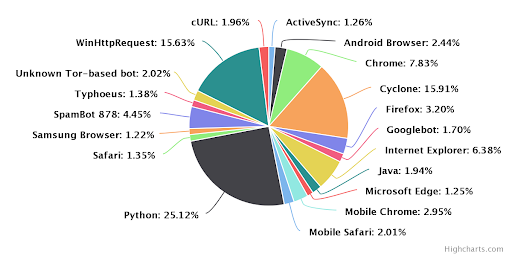
New Research: Crypto-mining Drives Almost 90% of All Remote Code Execution Attacks
It’s early in 2018 and we have already witnessed one of the top contenders in this year’s web application attacks. Continuing the trend from...
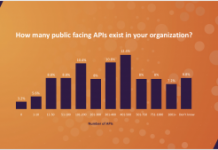
Survey: APIs a Growing Cybersecurity Risk
Like a lot of people, your mobile phone number is probably easily accessible to anyone with a bit of searching. Imagine if someone could...
Patched Facebook Vulnerability Could Have Exposed Private Information About You and Your Friends
In a previous blog we highlighted a vulnerability in Chrome that allowed bad actors to steal Facebook users’ personal information; and, while digging around...


![A Deep Dive into Database Attacks [Part III]: Why Scarlett Johansson’s Picture Got My Postgre Database to Start Mining Monero](http://www.dataproof.co.za/wp-content/uploads/2018/03/a-deep-dive-into-database-attacks-part-iii-why-scarlett-johanssons-picture-got-my-postgre-database-to-start-mining-monero-218x150.png)

![A Deep Dive into Database Attacks [Part IV]: Delivery and Execution of Malicious Executables through SQL Commands (MySQL)](http://www.dataproof.co.za/wp-content/uploads/2018/04/a-deep-dive-into-database-attacks-part-iv-delivery-and-execution-of-malicious-executables-through-sql-commands-mysql-218x150.png)