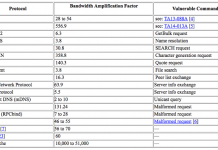
Inside a New DDoS Amplification Attack Vector via Memcached Servers
We recently saw a new DDoS amplification attack vector via memcached servers that culminated in two massive DDoS amplification attacks on February 28. Both...
Cloud Database Migration Peer Insights [Report]
Not long ago, for security, compliance or other reasons, it was unthinkable for many regulated organizations to move sensitive data into the cloud. It’s...
E-commerce: Bad bots are ready for the holidays. Are you?
The busiest time for online retailers is almost upon us—the holiday season. Each business is looking at ways to take advantage of cyber week...
RedisWannaMine Unveiled: New Cryptojacking Attack Powered by Redis and NSA Exploits
Recently cryptojacking attacks have been spreading like wildfire. At Imperva we have witnessed it firsthand and even concluded that these attacks hold roughly 90%...
Imperva Integration With AWS Security Hub: Expanding Customer Security Visibility
This article explains how Imperva application security integrates with AWS Security Hub to give customers better visibility and feedback on the security status of...
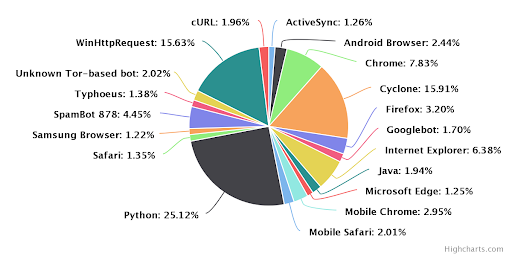
The Challenges of DIY Botnet Detection – and How to Overcome Them
Botnets have been around for over two decades, and with the rise of the Internet of Things (IoT) they have spread further to devices...
Microsoft and Imperva Collaboration Bolsters Data Compliance and Security Capabilities
This article explains how Imperva SecureSphere V13.2 has leveraged the latest Microsoft EventHub enhancements to help customers maintain compliance and security controls as regulated...
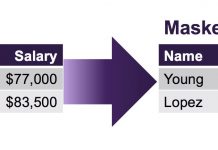
Three Reasons Why GDPR Encourages Pseudonymization
The General Data Protection Regulation (GDPR) is the European Union’s new data regulation designed to provide individuals with rights and protections over their personal...
Monitoring Data & Data Access to Support Ongoing GDPR Compliance – Part III: Tools
The new European Union (EU)-wide General Data Protection Regulation (GDPR) was signed into law in late April 2016, and the compliance deadline came into...
APIs Ease Customer Interaction — and External Attacks. Here’s how to Protect Them.
To deliver seamless service experiences to our customers, businesses now rely heavily on application programming interfaces (APIs). These are a non-negotiable aspect of the...


![Cloud Database Migration Peer Insights [Report]](http://www.dataproof.co.za/wp-content/uploads/2018/01/cloud-database-migration-peer-insights-report-218x150.png)