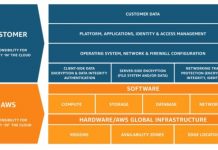
Cloud Migration Fundamentals: Overcoming Barriers to App Security [Infographic]
As more organizations move to the cloud, the line of responsibility in securing applications can become rather blurred.
The concept of control has historically rested...
Ransomware and malicious crypto miners in 2016-2018
Ransomware is not an unfamiliar threat. For the last few years it has been affecting the world of cybersecurity, infecting and blocking access to...
Achieve CIS Benchmarks for Cloud, Container and DevOps Environments
Achieve CIS Benchmarks for Cloud, Container and DevOps Environments #outlook a{ padding:0;...
Black Hat 2018
<img src="/sites/default/files/Blackhat-logo.png">
Join Digital Guardian at Black Hat 2018!
- Read more
Making Smarter Access Control Decisions
Hey Siri, block that attacker, please
Wouldn’t it be great if Siri, Alexa, or Google Assistant had the intelligence to figure out malicious intent, govern...
Pbot: evolving adware
The adware PBot (PythonBot) got its name because its core modules are written in Python. It was more than a year ago that we...
Zero Trust Security and DevOps Take the Crown at AWS Public Sector Summit 2018
Last week, Amazon Web Services hosted its AWS Public Sector Summit in Washington, DC. In its 9th year, the event attracted thousands of global...
How To Leverage Data Access Analytics for Effective Breach Detection
Detecting and preventing data breaches is a challenge for most, if not all, enterprises. In fact, according to a study released in 2017, 78%...
What’s the Financial Impact of Your VM Solution?
Tripwire, Inc.



![Cloud Migration Fundamentals: Overcoming Barriers to App Security [Infographic]](http://www.dataproof.co.za/wp-content/uploads/2018/07/cloud-migration-fundamentals-overcoming-barriers-to-app-security-infographic-218x150.png)