Last week, Amazon Web Services hosted its AWS Public Sector Summit in Washington, DC. In its 9th year, the event attracted thousands of global leaders and IT security practitioners from government, education, and non-profit organizations to learn how to start their path to the cloud or how to maintain momentum once they’ve begun the transformation.
BULLISH OUTLOOK FOR CLOUD ADOPTION IN GOVERNMENT
The meeting rooms and exhibit hall were humming and regularly required the organizer to cordon off access to the different floors due to reaching the facility’s capacity. The dramatic increase in attendees compared to prior years illustrates the growing appetite across the public sector for cloud services, which is driven by the promise of delivering services more efficiently and saving taxpayer dollars while modernizing legacy infrastructures.
According to Gartner, almost half of government organizations are actively using public cloud services and are expected to grow adoption by double-digits over the next three years.
In hundreds of conversations over a two-day period, it became apparent that most of government organizations have realized that more rapid adoption of public cloud services is crucial to remain mission-proficient. Due to its modern, elastic, standardized, and secure features, the cloud has become the favored method of driving adoption of new technology capabilities such as big data analytics, workflow automation, artificial intelligence, and many more.
CENTER OF DISCUSSION: ZERO TRUST SECURITY
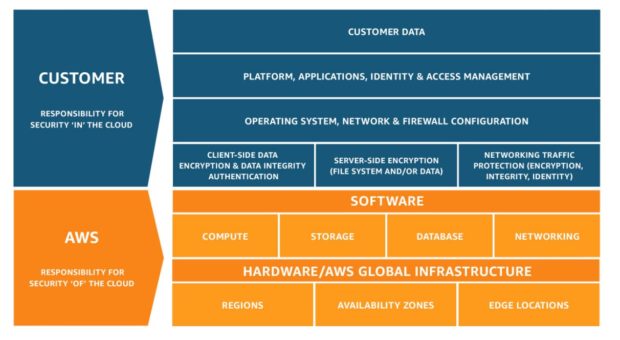
Another takeaway from the dialogue with practitioners was that the understanding of the Shared Responsibility Model has matured quite a bit, resulting in the need to augment AWS’ security best practices.

FIGURE 1: AWS Shared Responsibility Model
In this context, Zero Trust Security gained a lot of traction among attendees and was also seen as a dominant theme of many vendors’ exhibit displays. Transforming to the public cloud has many IT security professionals on their toes when it comes to security and therefore they’re buying into the fact that in today’s dynamic threat landscape the old mantra of “trust but verify” is no longer sufficient. Instead, we must assume that untrusted actors already exist ― both inside and outside the network. Trust must therefore be entirely removed from the equation.
The path to Zero Trust Security starts with Next-Gen Access to secure every user’s access to applications and infrastructure. Once an identity is authenticated and the integrity of the device is proven, authorization and access to resources is granted — but with just enough privilege necessary to perform the task at hand. This approach must be implemented across the entire organization, including public cloud environments, to minimize the risk of falling victim to a cyber-attack while at the same time achieving compliance.
The Centrify team demonstrated the ‘Six Best Practices for Increasing Security in AWS’ at its booth. This allowed attendees gain an understanding on how they can leverage Centrify’s Next-Gen Access solutions to:
- Extend their existing privileged access security solution by federating access to the AWS service, obviating the need for long-lived access keys;
- Extend enterprise authentication to EC2 instances by brokering identities from their choice of directory services — Active Directory, LDAP or Google;
- Extend enterprise identities to hosted applications with federated authentication for employees, business partners and customers; and
- Enforce MFA and Smart Card authentication to satisfy stringent security requirements and prove compliance.
THE EVER-EXPANDING ATTACK SURFACE: DEVOPS
Another hot topic at the AWS Public Sector Summit was secure DevOps. The hijacking of Tesla’s cloud-based DevOps platform is just one example that illustrates why these environments must be incorporated into the overall security strategy to cover an ever-expanding attack surface.
Considering this, AWS had carved out plenty of time in the summit agenda to explore ways on how to secure an organization’s application development environments by controlling access to the developer tools and infrastructure, enhancing application security, and auditing privileged activity.
Augmenting AWS’ optional IT operations and security tools, Centrify’s Next-Gen Access solutions help public sector organizations to scale adoption of secure DevOps by centralizing and automating access control to AWS infrastructure and your underlying developer toolchain.
To learn more about how Centrify helps establish secure DevOps, please visit our DevOps webpage.
CONCLUSION
Cloud adoption is inevitable for public sector organizations if they want to remain relevant to their mission. Applying Zero Trust Security by way of Next-Gen Access is vital when it comes to addressing security concerns that are still cited by industry analyst to be an inhibitor for public cloud adoption.
As the transition to the cloud also covers DevOps environments, the Zero Trust Security concept needs to be applied to this attack surface too. The desire to follow through with this new security strategy was visible at this year’s AWS Public Sector Summit and therefore makes me feel bullish about the future of cloud adoption in the public sector market.
The post Zero Trust Security and DevOps Take the Crown at AWS Public Sector Summit 2018 appeared first on Secure Thinking by Centrify.