Threats posed by using RATs in ICS
While conducting audits, penetration tests and incident investigations, we have often come across legitimate remote administration tools (RAT) for PCs installed on operational technology...
Stay Secure with Day-One Support for iOS 12 and macOS Mojave
It’s that time of year again: time for all the latest and greatest from our friends in Apple Park (or the Apple Spaceship as...
Microsoft and Imperva Collaboration Bolsters Data Compliance and Security Capabilities
This article explains how Imperva SecureSphere V13.2 has leveraged the latest Microsoft EventHub enhancements to help customers maintain compliance and security controls as regulated...
Integrating Security into DevOps Without Losing Momentum
Integrating Security into DevOps Without Losing Momentum #outlook a{ padding:0; } body{...
New trends in the world of IoT threats
Cybercriminals’ interest in IoT devices continues to grow: in H1 2018 we picked up three times as many malware samples attacking smart devices as...
Explainer Series: RDaaS Security and Managing Compliance Through Database Audit and Monitoring Controls
As organizations move to cloud database platforms they shouldn’t forget that data security and compliance requirements remain an obligation. This article explains how you...
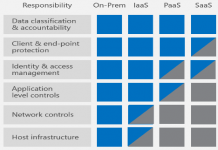
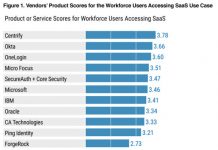
Centrify Scores Highest for Both “Workforce Users Accessing SaaS” and “Business-to-Business” in New Gartner...
Gartner just released their first ever “Critical Capabilities for Access Management, Worldwide, 2018” report, and we are proud to see that Centrify has scored...