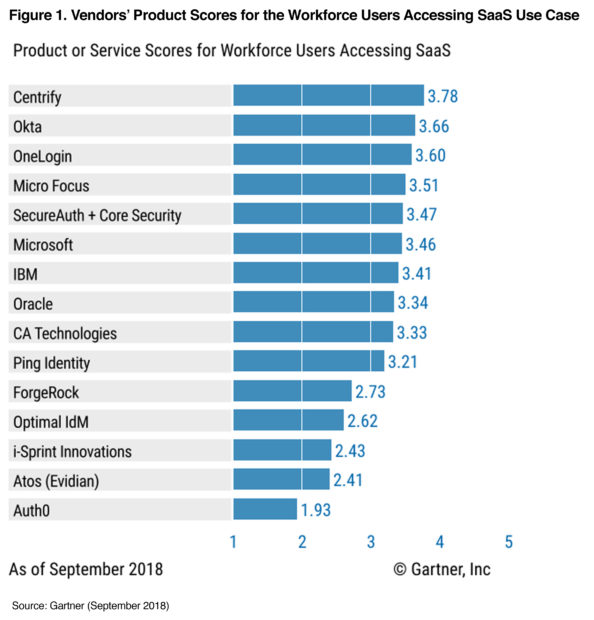
Gartner just released their first ever “Critical Capabilities for Access Management, Worldwide, 2018” report, and we are proud to see that Centrify has scored the highest of any vendor in 2 out of 3 Use Cases including “Workforce Users Accessing SaaS” (3.78 out of 5.0) and “Business-to-Business” (3.52 out of 5.0). Gartner evaluated 15 vendors’ services on nine critical capabilities including Event Logging and Reporting, SaaS Application Enablement, User Authentication Methods, and Authorization and Adaptive Access and three common Use Cases: Workforce Users Accessing SaaS, Business-to-Business, and Business-to-Consumer.
We believe this validates our unique ability to secure access to apps and endpoints. Please have a look at a complimentary copy of the full report to see for yourself.
Gartner defines the “Workforce Users Accessing SaaS” Use Case as:
“This use case involves the setup of connections from the AM to SaaS, and the protection of that access with authentication, SSO and authorization functions.”
We’re especially proud of this ranking, as we believe it’s based solely on demonstration of product capabilities — all of which were built based on real customer need. Centrify has been building enterprise-critical solutions since 2004, and we feel that this report, along with our 95% customer retention rate, helps to underscore our commitment to our customers’ security and success.
Additionally, we are excited about the results of the Business-to-Business (B2B) Use Case, which Gartner defines as:
“This use case involves business partner users accessing a potentially wide range of applications that do or do not support federated SSO standards and are hosted anywhere.”
If customers are the lifeblood of a company, that organization’s network of partners, suppliers and vendors are the value chain that the company depends on to service and retain those customers. B2B access management reduces friction along this value chain while also mitigating a vital attack vector. (According to Ponemon, 56% of organizations have had a breach that was caused by one of their vendors.)
A True Test is Always Best
I personally love this report both as a marketer of a leading Next-Gen Access product but even more so as a former IT buyer and technology implementer. I depended on neutral product reviews and evaluations to understand what will work best for my business. This report is just that. It’s truly a product evaluation — based on the use cases that customers need most. This is not a website comparison. This isn’t about who has the slickest collateral. It’s not about what vendors are most popular at a given moment. This is a true test — based on actual product capabilities and demonstration.
In Gartner’s words from the report:
In defining the product/service category for evaluation, the analyst first identifies the leading uses for the products/services in this market. What needs are end-users looking to fulfill, when considering products/services in this market? Use cases should match common client deployment scenarios. These distinct client scenarios define the Use Cases.
The analyst then identifies the critical capabilities. These capabilities are generalized groups of features commonly required by this class of products/services. Each capability is assigned a level of importance in fulfilling that particular need; some sets of features are more important than others, depending on the use case being evaluated.
Each vendor’s product or service is evaluated in terms of how well it delivers each capability, on a five-point scale. These ratings are displayed side-by-side for all vendors, allowing easy comparisons between the different sets of features.
We believe the report is clear on what use cases were tested and the scoring and ranking methodologies for each. It’s easy to rank the capabilities that are critical for specific businesses. It’s a great tool for folks looking to understand the differences between Access Management products.
Centrify continually strives to offer helpful Access Management evaluation tools, such as this IDaaS buyer’s guide, to assist you when you are considering a solution. But I am particularly proud of the result of this Gartner report as it is an unbiased and comprehensive review of the Access Management Products in the market and I hope it is useful as you examine the alternatives that make the most sense for your organization.
Access your complimentary copy of the “Critical Capabilities for Access Management, Worldwide” report here.
Gartner “Critical Capabilities for Access Management, Worldwide” by Gregg Kreizman September 2018.
These graphics were published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Centrify.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and is used herein with permission. All rights reserved.
The post Centrify Scores Highest for Both “Workforce Users Accessing SaaS” and “Business-to-Business” in New Gartner Report appeared first on Secure Thinking by Centrify.