GDPR and Privacy: How to Earn the Trust of Your Customers and Keep Regulators...
Customer data is the lifeblood of any organisation and the key to unlocking sales and growth. But the data you hold and how you...
Real-Life Exposed Privileged Identity Theft
Have you ever had your identity stolen? Credit cards obtained under your name that were not yours?
Most of us have, and what a pain...
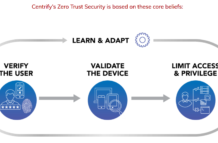
Six Reasons to Experience Zero Trust Security in Centrify Booth 501 at RSA
In case you hadn’t heard, the 2018 RSA Conference will be held April 16-19 at the Moscone Center in San Francisco. If you haven’t...
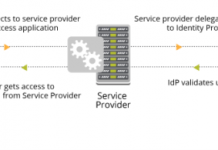
Making Headlines: SAML
On February 27, 2018 the CERT Division of Carnegie Mellon University’s Software Engineering Institute issued advisory #475445, outlining a design flaw in Security Assertion...
Centrify for NIST 800-171 MFA Compliance
I often speak with Federal System Integrators (FSIs) who need to implement Multi-Factor Authentication (MFA) as part of their NIST 800-171 compliance.
Specifically section 3.5.3...
SEC Clarification: Companies Must Disclose Breaches
In late February, the U.S. Security and Exchange Commission (SEC) issued new cybersecurity guidance in the form of an “interpretive release.” According to the...
Frost & Sullivan Recognizes Centrify for IDaaS and PIM Leadership
Today Frost & Sullivan, a leading analyst firm and growth partnership company, announced that Centrify has earned the North American Product Leadership Award for...
With Less Than 100 Days to Go, How to Get C-Level Buy-in for GDPR...
For GDPR compliance initiatives to work effectively, there has to be buy-in from the boardroom. That doesn’t just mean releasing the necessary funds to...
Takeaways from the Russia-Linked US Senate Phishing Attacks
The Zero Trust Security approach could empower organizations and protect their customers in ways that go far beyond typical security concerns.
On January 12, 2018,...
Multi-factor Authentication (MFA) Is Ready for Prime Time
We’ve heard it time and again. As security threats increase and morph, and user devices and locations diversify, multi-factor authentication (MFA) should be blossoming...