Have you ever had your identity stolen? Credit cards obtained under your name that were not yours?
Most of us have, and what a pain it can be to stop excess charges, get reimbursed, close down those accounts, and repair your damaged credit. It can take years to recover from such an invasion.
While we know what it’s like in our personal lives, many of us don’t pay attention to the damage that could be caused in our professional careers, especially with privileged accounts like database access.
One reason for this disconnect is because the breaches typically are not financial in nature where money can just be credited. What’s being stolen is data and intellectual property that once obtained can be assumed to be gone forever. It’s digital currency that can be stored anywhere and transferred at any moment, there is simply no way to recover from a breach with 100 percent certainty.
So how easy is it to steal your credentials in practice? With very little internet research any rookie hacker can harvest plenty of privileged passwords.
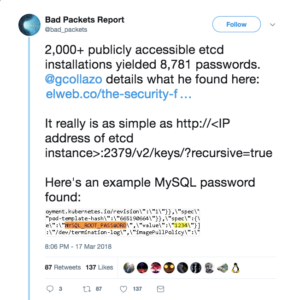
A blog posted very recently by researcher Giovanni Collazo showed a simple query found thousands of servers operated by businesses and other organizations are openly sharing credentials that may allow anyone on the Internet to log in and read or modify potentially sensitive data stored online.
His quick search found almost 2,300 Internet-exposed servers running etcd, a type of database that computing clusters and other types of networks use to store and distribute passwords and configuration settings needed by various servers and applications.
Most developers are aware of and take care to protect their data in databases such as MySQL, PostgreSQL and MongDB, but what about databases that don’t feel like “regular databases,” like Memcached, Redis and etcd?
etcd comes with a programming interface that responds to simple queries that, by default, return administrative login credentials without first requiring authentication. The passwords, encryption keys, and other forms of credentials are used to access MySQL and PostgreSQL databases, content management systems, and other types of production servers.
Collazo wrote a simple script designed to obtain any credentials exposed on the servers.
GET http://<ip address>:2379/v2/keys/?recursive=true
After collecting a mere 750MB of data from almost 1,500 servers he found:
- 8,781 passwords
- 650 Amazon Web Services access keys
- 23 secret keys
- 8 private keys
YIKES!
In a related article by Dan Goodin of Ars Technica, researcher Troy Mursch independently verified Collazo’s findings and found even worse: default passwords of “1234.” He posted this image:

Surprised? You shouldn’t be, especially when we know from Verizon’s 2017 Data Breach Investigations Report that 81% of hacking-related breaches leveraged stolen, weak, or default passwords.
Putting proper Privileged Access Management (PAM) controls in place can fairly easily mitigate this type of exposure. Federate your access to privileged servers with short-lived tokens rather than static credentials (Single Sign-On), employ multi-factor authentication (MFA) for access to any sensitive resources, or simply store those credentials and keys in a protected vault and rotate.
The post Real-Life Exposed Privileged Identity Theft appeared first on Secure Thinking by Centrify.