C-Suite Disconnect is Weakening Cybersecurity
Today, Centrify announced a new research study conducted with Dow Jones Customer Intelligence titled, “CEO Disconnect is Weakening Cybersecurity.” The report sheds light on...
Break the Trust and Stop the Breach: The Zero Trust Security Model
As 2018 is upon us, it’s time to take stock of our new realities and commit to better behavior that benefits us and our...
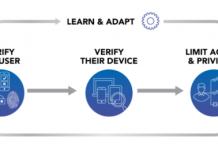
Five Best Practices for Zero Trust Security
The Centrify Zero Trust Security model is effective because it allows organizations to remove trust from the equation entirely. Based on the assumption that...
Zero Trust Security for the New Australian Data Breach Law
Many Australian businesses need to rethink their approach to security to prepare for their nation’s new mandatory data breach notification law which take effect...
Escaping Data-Breach Groundhog Day
Countless companies globally are trapped in data breach Groundhog Day, unable to escape a repeating cycle of cyber attacks.
In the 2018 Thales Data Threat...
What do Equifax, HBO, Uber and Yahoo All Have in Common?
A consumer ratings agency, a cable network, a transportation company and a web services provider. What ties them together? Sure, they were all impacted...
Centrify to Discuss Zero Trust Security at the ICIT 2018 Winter Summit
Following the high-profile breach of the US Office of Personnel Management (OPM), which exposed the personal data of millions of Americans, the House of Representatives’...
4 Months to Go: A New Year GDPR Checklist
As we enter the New Year, IT and security leaders have most likely been glued to revelations of major new CPU-level vulnerabilities Meltdown and...
Data Breaches Plague Organizations for Years
Once an organization’s network is breached, extinguishing the flames is just the first step in a long, painful and costly journey to recovery. There’s...
The Emerging Importance of Securing Access to AWS
With 50,000 attendees, over 1,000 breakout sessions and countless sponsors and exhibitors, the 2017 AWS re:Invent conference in Las Vegas was one of the...