There is a great exposé in the New York Times breaking down the timeline and mis-steps in response to the fire that occurred in the Notre-Dame Cathedral in Paris in April, 2019. Reading through the article, what I kept thinking about were the interesting parallels between fire response and cyber threat response.
What stood out to me immediately in the article was this idea in forensic analysis from Glenn Corbett, an associate professor of fire science at John Jay College of Criminal Justice in New York:
“You have a system that is known for its ability to detect very small quantities of smoke. Yet the whole outcome of it is this clumsy human response. You can spend a lot to detect a fire, but it all goes down the drain when you don’t move on it.”
For anyone responsible for cybersecurity protection and threat response – and hopefully any rapid response that minimizes damages — that quote should carry resonance. Going further, I thought I’d write about a number of interesting parallels between the world of threat response to fires and cyber-attacks made painfully clear reading about this timeline of response.
NOTRE-DAME LESSONS FOR CYBERSECURITY RESPONSE
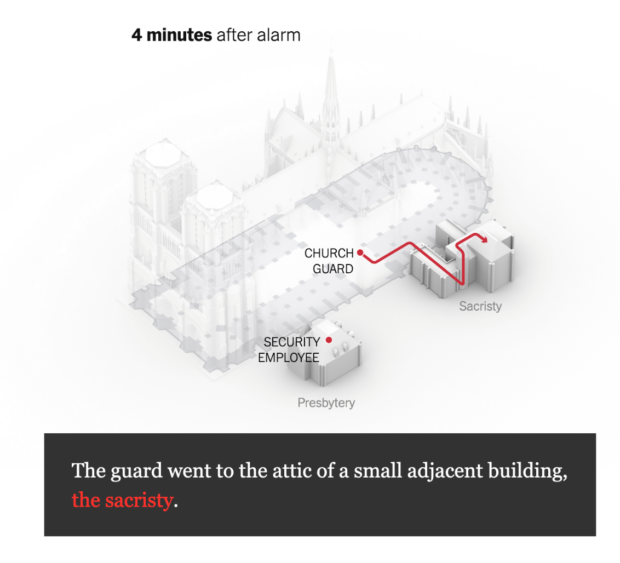
Lesson 1: Sophisticated alerting frameworks, without accurate, actionable results don’t get you very far. For the first responders in the Notre-Dame incident, complex alerts that didn’t easily show alert locations led to nearly-catastrophic delays in response times.
In fact, a misinterpretation of the location of the very first alert sent the fire management team to the wrong building.
(Image courtesy of New York Times, “Notre-Dame came far closer to collapsing than people knew” by Elian Peltier, James Glanz, Mika Gröndahl, Weiyi Cai, Adam Nossiter and Liz Alderman, 7/18/2019)
Lesson 2: Complex systems are harder to intrinsically trust. Herein lies likely a more subtle, more “human” behavior: this very sophisticated smoke-detection system (which the Notre-Dame administration reportedly spent over €6 million and six years to implement) sent very arcane, detailed information about the chemical construction of the smoke. Upon not finding fire in an outer building “The Sacistry,” the responder more than likely didn’t trust the alerting system, giving up too soon, as opposed to working harder to find the smoke. Overly complex systems can impact both signal clarity and user trustworthiness.
Lesson 3: Employee retention = breach prevention. You are only as good as your human links in the chain. Automation and detection are great…but when an employee three days on the job is monitoring those alerts, and workers are on second shifts and overtime, painful mistakes can occur. It’s not clear if more job training or more practice scenarios could have avoided the costly routing problems that led to a 30-minute delay in locating the actual fire, but it’s clear that from a breach (or fire) prevention standpoint, employee retention is greater than employee training. People on the job longer tend to make fewer mistakes.
Lesson 4: In Cyber and Fire Response, delayed response means more time for more damage. In the Notre-Dame fire, lots of elements–bad luck, new hires, supervisors being unreachable, and workers fatigued by over-time shifts—combined to make a slow response even slower or more cumbersome. A plan never survives the first battle, but even in a building 900 years old, any prevention plan should expect many co-dependent things to go wrong at the same time.
Fortunately for Parisians and all admirers of singular, spectacular, spiritual architecture, the firepeople ultimately triumphed, the Cathedral ultimately withstood, and no lives were lost fighting the fires at Notre-Dame.
Will your organization be as lucky if a catastrophic cybersecurity event breaks out in your organization?
The post On Systems, Smoke Alerts, and Lessons Learned from The Paris Notre-Dame Cathedral Fire appeared first on Secure Thinking by Centrify.