Zero Trust Security and DevOps Take the Crown at AWS Public Sector Summit 2018
Last week, Amazon Web Services hosted its AWS Public Sector Summit in Washington, DC. In its 9th year, the event attracted thousands of global...
Adopt Next-Gen Access to Power Your Zero Trust Strategy
Security breaches are now all too commonplace — 58% of organizations have experienced at least one in the past 12 months. As a result,...
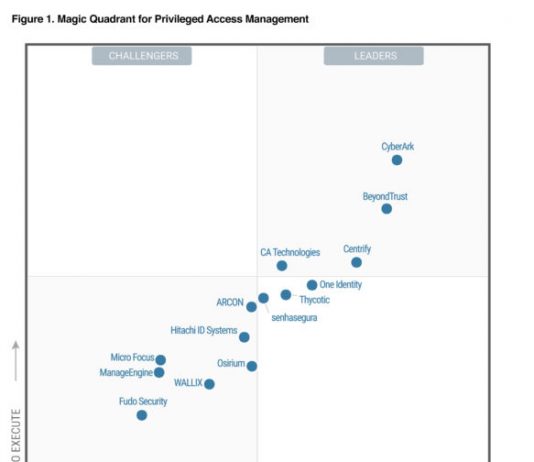
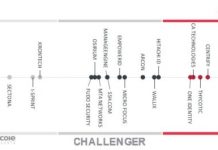
3 for 3! Centrify a Leader in 2019 KuppingerCole Leadership Compass for PAM
KuppingerCole recently published its 2019 KuppingerCole Leadership Compass for Privileged Access Management (PAM), again recognizing Centrify as a Leader as it did in the...
Centrify Zero Trust Security Partners in the Spotlight at RSA Booth 501
RSA Conference has moved back to April this year, and next week the largest cybersecurity trade show in the world will once again convene...
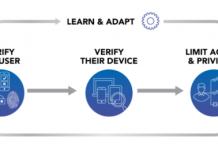
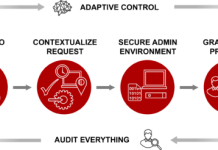
Five Best Practices for Zero Trust Security
The Centrify Zero Trust Security model is effective because it allows organizations to remove trust from the equation entirely. Based on the assumption that...
Persistence Pays Off
There are lots of maxims in the startup world about passion, patience and perseverance — but most of the time it is just lip...
Moving Beyond Legacy PAM: Centrify Zero Trust Privilege
Our customers trust us to keep their most privileged credentials – the “keys to the kingdom” – secure from being exploited. Over half of...
The Year in Review: Rethink Security
During a year of high-profile breaches like Equifax, HBO and Uber, as well as the realization that Yahoo’s highly-publicized 2013 breach compromised the accounts...
Centrify to Discuss Zero Trust Security at the ICIT 2018 Winter Summit
Following the high-profile breach of the US Office of Personnel Management (OPM), which exposed the personal data of millions of Americans, the House of Representatives’...
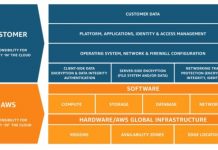
The Cost of Customer Identity & Access Management (CIAM)
Customer Identity and Access Management (CIAM) is essentially a set of tools that allow your business to securely authenticate, manage and engage customers who...