Our customers trust us to keep their most privileged credentials – the “keys to the kingdom” – secure from being exploited. Over half of the Fortune 100, the world’s largest financial institutions, intelligence agencies, and critical infrastructure companies, all trust Centrify to stop the leading cause of breaches – privileged credential abuse.
We know that we can do even better.
That starts today with a singular focus on continuing to redefine the legacy approach to Privileged Access Management (PAM) with cloud-architected Zero Trust Privilege.
SO WHAT DOES THAT MEAN?
First, to sharpen that focus, we’re spinning out our Identity-as-a-Service business as a separate company called Idaptive. Centrify is doubling down on Privilege Access Management with more dedicated resources to optimize focus, efficiency, customer success and growth.
Second, we firmly believe that the legacy methods of managing privileged access do not address the use cases of modern enterprises. Privileged access is no longer constrained to systems and resources inside the network such as infrastructure, databases, and network devices. It is extended to an expanded threatscape that includes cloud environments, big data projects, DevOps, containers and more. When 80 percent of breaches involve privilege credentials, it’s clearly too easy.
Finally, when a legacy PAM solution will not suffice – a cloud-architected, Zero Trust Privilege solution must emerge that will empower a “never trust, always verify, enforce least privilege” approach.
To rise above, Centrify is focused on increasing our leadership position in the market with a vision backed by innovation, best practices, and strong execution.
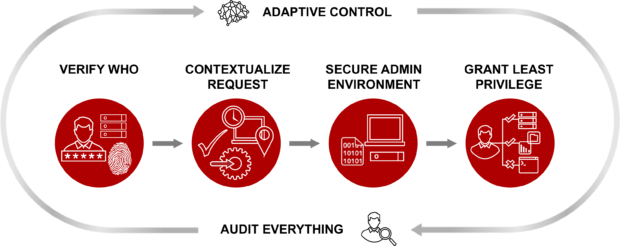
At the center of that is Centrify Zero Trust Privilege, which helps customers grant least privilege access based on verifying who is requesting access, the context of the request and the risk of the access environment. By implementing least privilege access, Centrify minimizes the attack surface, improves audit and compliance visibility, and reduces risk, complexity and costs for the modern, hybrid enterprise.
CONTINUING THE ZERO TRUST JOURNEY
I’m very excited to lead Centrify on this journey. Note that I don’t consider it a new journey – it’s a path we’ve already been on for quite a while as the company has evolved into a Zero Trust Security leader under Tom Kemp’s leadership. Tom is still active at Centrify and will remain involved as a strategic advisor as we make this transition.
I will also reiterate that we are doing this because it is the best way to serve our customers. We hope you’ll agree that a more focused Centrify will better enable your organization as you continue your focus on securing the modern enterprise through Zero Trust Privilege.
The post Moving Beyond Legacy PAM: Centrify Zero Trust Privilege appeared first on Secure Thinking by Centrify.