Multi-factor Authentication (MFA) Is Ready for Prime Time
We’ve heard it time and again. As security threats increase and morph, and user devices and locations diversify, multi-factor authentication (MFA) should be blossoming...
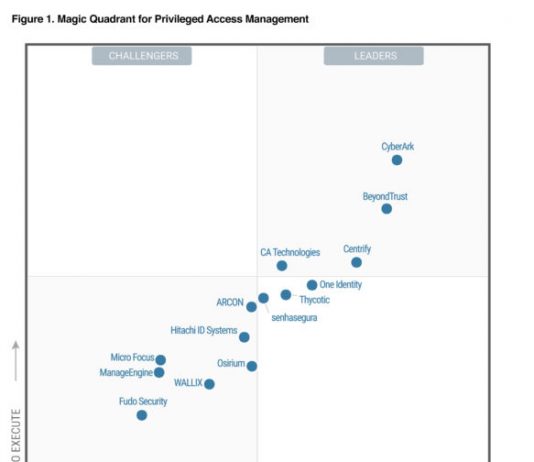
Centrify Launches Zero Trust Security Network Ecosystem
The world has changed. I’m not sure if it was the HBO breach, Equifax, Yahoo, or one of the many breaches since, but after...
C-Suite Disconnect is Weakening Cybersecurity
Today, Centrify announced a new research study conducted with Dow Jones Customer Intelligence titled, “CEO Disconnect is Weakening Cybersecurity.” The report sheds light on...
Escaping Data-Breach Groundhog Day
Countless companies globally are trapped in data breach Groundhog Day, unable to escape a repeating cycle of cyber attacks.
In the 2018 Thales Data Threat...
Zero Trust Security for the New Australian Data Breach Law
Many Australian businesses need to rethink their approach to security to prepare for their nation’s new mandatory data breach notification law which take effect...
Six Reasons to Experience Zero Trust Security in Centrify Booth 501 at RSA
In case you hadn’t heard, the 2018 RSA Conference will be held April 16-19 at the Moscone Center in San Francisco. If you haven’t...
4 Steps to Reduce the Risk of Shared Account Passwords
Reduce the Risk of a Security Breach When Sharing Privileged Accounts
There are partners, employees, contractors, customers and others who access or try to access...
What do Equifax, HBO, Uber and Yahoo All Have in Common?
A consumer ratings agency, a cable network, a transportation company and a web services provider. What ties them together? Sure, they were all impacted...
GDPR and Privacy: How to Earn the Trust of Your Customers and Keep Regulators...
Customer data is the lifeblood of any organisation and the key to unlocking sales and growth. But the data you hold and how you...
Break the Trust and Stop the Breach: The Zero Trust Security Model
As 2018 is upon us, it’s time to take stock of our new realities and commit to better behavior that benefits us and our...