FIN7.5: the infamous cybercrime rig “FIN7” continues its activities
On August 1, 2018, the US Department of Justice announced that it had arrested several individuals suspected of having ties to the FIN7 cybercrime...
NASCIO CIO Top Priorities in a Zero Trust World
Many state CIOs are struggling to manage the onslaught of priorities that are captured in the NASCIO Top 10 Policy and Technology Priorities for...
APT trends report Q1 2019
For just under two years, the Global Research and Analysis Team (GReAT) at Kaspersky Lab has been publishing quarterly summaries of advanced persistent threat...
I know what you did last summer, MuddyWater blending in the crowd
Introduction
MuddyWater is an APT with a focus on governmental and telco targets in the Middle East (Iraq, Saudi Arabia, Bahrain, Jordan, Turkey and Lebanon)...
Centrify Achieves FedRAMP Authorization
Centrify received exciting news this week that we are now FedRAMP Authorized!
For those who don’t know about FedRAMP, it is a government-wide program that...
Subscriber Services
Read more
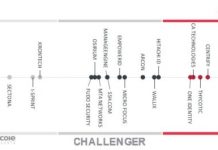
3 for 3! Centrify a Leader in 2019 KuppingerCole Leadership Compass for PAM
KuppingerCole recently published its 2019 KuppingerCole Leadership Compass for Privileged Access Management (PAM), again recognizing Centrify as a Leader as it did in the...
Operation ShadowHammer: a high-profile supply chain attack
In late March 2019, we briefly highlighted our research on ShadowHammer attacks, a sophisticated supply chain attack involving ASUS Live Update Utility, which was...