Financial Cyberthreats in 2017
In 2017, we saw a number of changes to the world of financial threats and new actors emerging. As we have previously noted, fraud...
IoT hack: how to break a smart home… again
There can never be too many IoT gadgets – that’s what people usually think when buying yet another connected device with advanced functionality. From...
Multi-factor Authentication (MFA) Is Ready for Prime Time
We’ve heard it time and again. As security threats increase and morph, and user devices and locations diversify, multi-factor authentication (MFA) should be blossoming...
Subscribe to Data Insider
Subscribe to <span style="color: #11111; font-style: bold; letter-spacing: -1px;">DATA</span><span style="color: #E51892; font-style: italic; font-style: bold; letter-spacing: -1px;">INSIDER</span>
.blog_subscribe_block{ margin-top: 50px !important; margin-left: auto;...
Tax refund, or How to lose your remaining cash
Every year, vast numbers of people around the globe relish the delightful prospect of filling out tax returns, applying for tax refunds, etc. Given...
C-Suite Disconnect is Weakening Cybersecurity
Today, Centrify announced a new research study conducted with Dow Jones Customer Intelligence titled, “CEO Disconnect is Weakening Cybersecurity.” The report sheds light on...
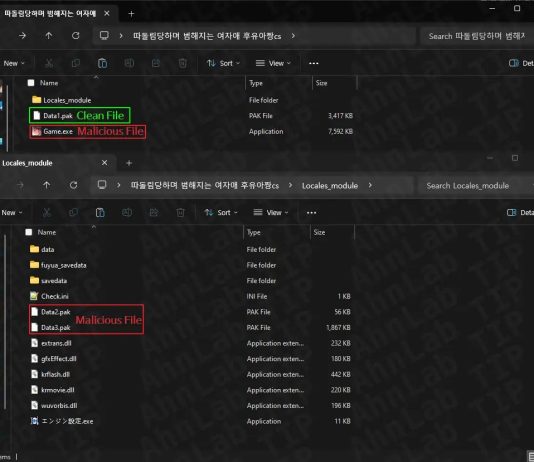
A Slice of 2017 Sofacy Activity
Sofacy, also known as APT28, Fancy Bear, and Tsar Team, is a highly active and prolific APT. From their high volume 0day deployment to...
Break the Trust and Stop the Breach: The Zero Trust Security Model
As 2018 is upon us, it’s time to take stock of our new realities and commit to better behavior that benefits us and our...
Spam and phishing in 2017
Figures of the year
The share of spam in mail traffic came to 56.63%, down 1.68% against 2016.
The biggest source of spam remains the US...
Five Best Practices for Zero Trust Security
The Centrify Zero Trust Security model is effective because it allows organizations to remove trust from the equation entirely. Based on the assumption that...