A predatory tale: Who’s afraid of the thief?
In mid-February, Kaspersky Lab received a request for incident response from one of its clients. The individual who initially reported the issue to our...
Financial Cyberthreats in 2018
Introduction and Key Findings
The world of finance has been a great source of income cybercriminals across the world due to an obvious reason –...
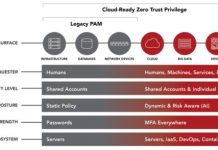
Time to Retire “The Year Of…” at RSA 2019
Today at the RSA Security Conference, we announced Centrify’s Cloud-Ready Zero Trust Privilege Services architecture, including a wide range of enhancements that redefine legacy...
Centrify RSA Booth 6445: Where Zero Trust Privilege Partners Take the Stage
If there was one clear takeaway from the 2018 RSA Conference, it was that Zero Trust was ready to take off.
It seemed like everywhere...
DoT for RPZ distribution
Read more
Start Your Engines! It’s Zero Trust Privilege Test Drive Season!
As organizations struggle to protect the ever-expanding attack surface, they not only have to secure access to infrastructure, databases, and network devices, but also...
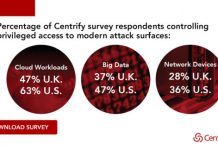
NEW CENTRIFY SURVEY: Too Much Privilege, Not Enough PAM Powered by Zero Trust
I’m both a technology guy, and a numbers guy.
I have Bachelor of Science degrees in both Accounting and Computer Science. I’ve held the CFO...
How to Attack and Defend a Prosthetic Arm
The IoT world has long since grown beyond the now-ubiquitous smartwatches, smartphones, smart coffee machines, cars capable of sending tweets and Facebook posts and...
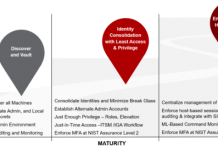
Gartner Names PAM a Top Security Project (AGAIN!) in 2019
Last June at the 2018 Gartner Security & Risk Management Summit, the analyst firm issued a “Smarter with Gartner” paper outlining the Top 10...