Recent Cloud Atlas activity
Also known as Inception, Cloud Atlas is an actor that has a long history of cyber-espionage operations targeting industries and governmental entities. We first...
Centrify Mid-Year Data Breach Report: Credential Abuse One of the Top Threats of Cyber...
It’s hard to believe that we’re already more than halfway through 2019. Or as I like to put it, I’ve already wasted one month...
DDoS attacks in Q2 2019
News overview
The second quarter of 2019 turned out to be richer than the first in terms of high-profile DDoS attacks. True, most of the...
APT trends report Q2 2019
For two years, the Global Research and Analysis Team (GReAT) at Kaspersky has been publishing quarterly summaries of advanced persistent threat (APT) activity. The...
Financial threats in H1 2019
Introduction and methodology
Financial cyberthreats are malicious programs that attack users of online banking services, electronic money, cryptocurrency and other similar services, as well as...
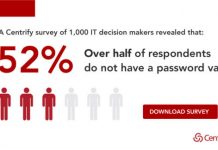
52% of Companies Don’t have a Password Vault for Privileged Access – Here’s Your...
Over the first half of 2019, Centrify issued two research reports about the adoption of Privileged Access Management (PAM) solutions and the maturity of...
How to steal a million (of your data)
Any user data — from passwords for entertainment services to electronic copies of documents — is highly prized by intruders. The reason is simply...
On the IoT road: perks, benefits and security of moving smartly
Kaspersky has repeatedly investigated security issues related to IoT technologies (for instance, here, or here). Earlier this year our experts have even gained foothold...