Explainer Series: What is Clickjacking?
Here we go, another online trap ready to ensnare unsuspecting – well, until now anyway – users. As if Phishing, Cryptojacking, credential stuffing and...
Static vs Dynamic Data Masking: Why Are We Still Comparing the Two?
Earlier this month a leading analyst released their annual report on the state of Data Masking as a component of the overall Data Security...
Read: Apache Struts Patches ‘Critical Vulnerability’ CVE-2018-11776
On August 22, Apache Struts released a security patch fixing a critical remote code execution vulnerability. This vulnerability has been assigned CVE-2018-11776 (S2-057) and...
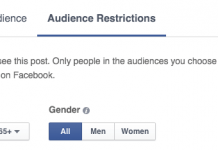
A Bug in Chrome Gives Bad Actors License to Play ‘20 Questions’ with Your...
In a 2013 interview with The Telegraph, Eric Schmidt, then CEO of Google was quoted as saying: “You have to fight for your privacy...
Watch: An Account Takeover Attack Using Credential Stuffing, and How to Protect Against It...
As cryptocurrencies continue to grow in diversity, so too do the threats they face, specifically those targeting the cryptocurrency exchange. Now, more than ever,...
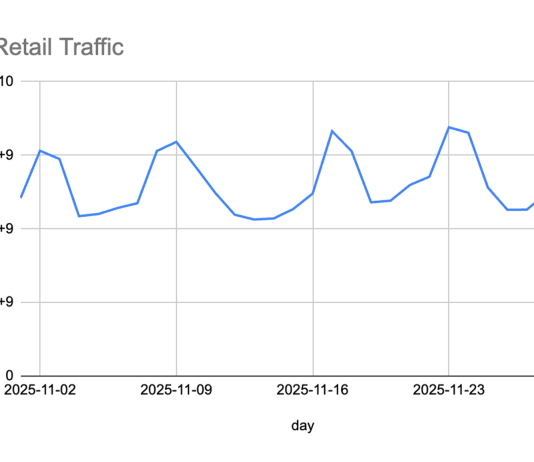
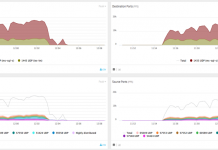
Enhanced Infrastructure DDoS Protection Analytics: Targeted Visibility for Greater Accuracy
We’ve rolled out enhanced infrastructure protection analytics which shows top traffic patterns for traffic flowing through our Incapsula Infrastructure DDoS Protection service.
Imperva clients can...
Onwards and Upwards: Our GDPR Journey and Looking Ahead
At Imperva, our world revolves around data security, data protection, and data privacy. From our newest recruits to the most seasoned members of the...
A Quick-Start Introduction to Database Security: An Operational Approach
The recent SingHealth data breach incident exposed around 1.5 million patients’ records. In its aftermath, the Cyber Security Agency of Singapore published a set...
Imperva to Acquire DevOps Security Leader Prevoty
Today, we announced that we entered into an agreement to acquire Prevoty, an innovator and leader in building application security that can block attacks...
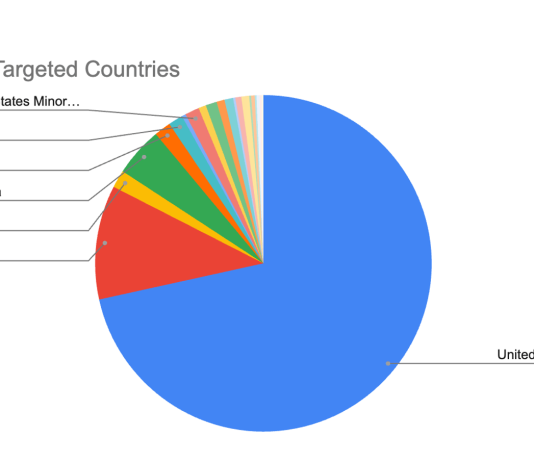
Fortnite Scammers Approaching $1m in Annual Takings
When something seems too good to be true, it probably is. It’s a hard lesson to learn and, in this case, one that’s being...