Personalized Customer Support that Garners a Personalized Thank You
In my two-plus years as a Technical Support Engineer at Imperva, I’ve handled a wide variety of customer cases. And I’ve had the satisfaction...
Introducing Imperva Cloud Data Security!
We at Imperva are gearing up for the inaugural AWS re:Inforce event on June 25th and 26th in Boston, Massachusetts, where technical leaders will...
UK’s Largest Mobile Carrier Relies on AWS and Imperva FlexProtect for Web Delivery and...
In today’s highly-competitive telecommunications market, the website is integral to successful and fast customer service. Downtime due to intrusion, data breach, or DDoS attack...
Every Second Counts When You’re Under Attack — Imperva Provides 3 Second DDoS Mitigation,...
Let’s be blunt: cybersecurity is a never-ending arms race between bad actors and IT and security teams. Lately, attackers have surged. Armed with powerful,...
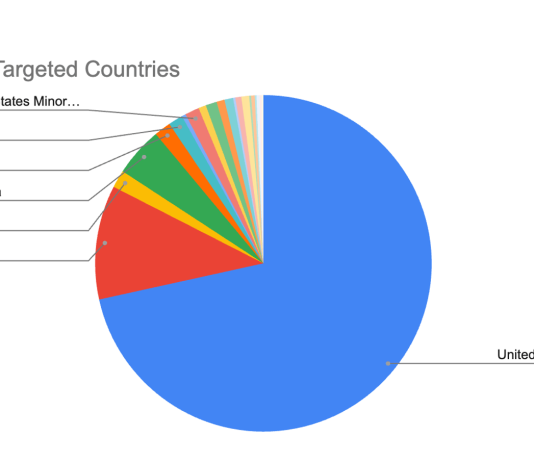
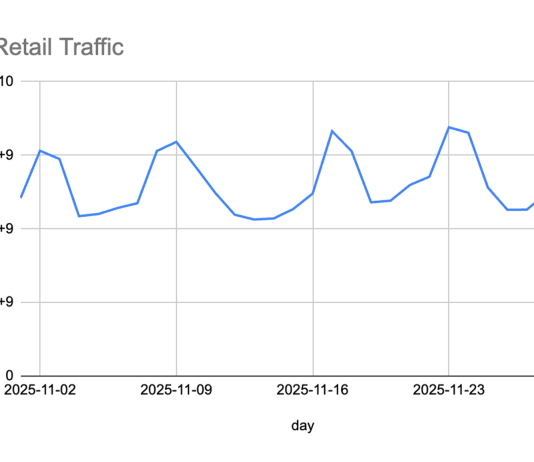
SQL Injection Attacks: So Old, but Still So Relevant. Here’s Why (Charts)
We’re living in the Golden Age of data. Some companies analyze it to better themselves, others trade it for profit, none give it up...
The Struggle is Real
We’ve all heard the phrase, “We live in a male dominated world.” This phrase is most often delivered with a negative connotation when someone...
Imperva to Acquire Distil Networks, the Leader in Advanced Bot Mitigation
As an established leader in cybersecurity, Imperva provides our customers the most comprehensive, analyst-recognized application security solution on the market. We are a five-time...
Web Security Leader Rapidly Expands by Partnering with AWS and Imperva
Companies try to plan and pace their growth. Those plans go out the window when a merger or acquisition happens, as it did to...
Infonomics-based Model Teaches CISOs how to Assess their Data’s Financial Risk, Invest Properly in...
Here’s what I consider the biggest contradiction in cybersecurity: the most-financially-damaging, reputation-destroying security incidents almost always involves the theft of millions of database records....
Cloud WAAPs Are the Future of Application Security. But What Does That Mean?
Millions of Verizon FIOS broadband users vulnerable to hackers controlling and surveilling their home networks.
Thousands of GPS watches whose maps were open to attackers...