Q4 2017 Global DDoS Threat Landscape Report
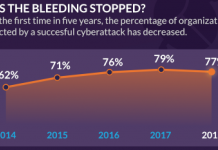
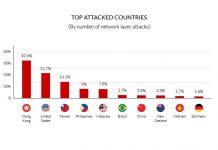
Today we are releasing our latest Global DDoS Threat Landscape Report, a statistical analysis of 5,055 network and application layer DDoS attacks mitigated by...
Data Security Solutions for GDPR Compliance
Enforcement of the new EU General Data Protection Regulation (GDPR) adopted in 2016 starts on May 25, 2018. It requires all organizations that do...
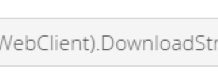
A Deep Dive into Database Attacks [Part III]: Why Scarlett Johansson’s Picture Got My...
As part of Imperva’s efforts to protect our customers’ data, we have an ongoing research project focused on analyzing and sharing different attack methods...
RedisWannaMine Unveiled: New Cryptojacking Attack Powered by Redis and NSA Exploits
Recently cryptojacking attacks have been spreading like wildfire. At Imperva we have witnessed it firsthand and even concluded that these attacks hold roughly 90%...
2018 Cyberthreat Defense Report: Where IT Security Is Going
What keeps you awake at night? We asked IT security professionals the same question and found that these issues are top of mind: malware...
Hunting for Insider Threats: Using Activity Modeling to Detect Suspicious Database Commands and Access...
The Widening Gap
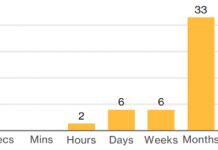
Data breaches by insiders are very challenging to catch. The gap between the rise of insider threats and speed of hunting them...
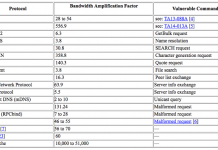
Inside a New DDoS Amplification Attack Vector via Memcached Servers
We recently saw a new DDoS amplification attack vector via memcached servers that culminated in two massive DDoS amplification attacks on February 28. Both...
NEW: Vulnerability and Assessment Scanning for Your AWS Cloud Databases
Scuba is a free and easy-to-use tool that uncovers hidden security risks. Scuba is frequently updated with content from Imperva’s Defense Center researchers.
With Scuba...
New Research: Crypto-mining Drives Almost 90% of All Remote Code Execution Attacks
It’s early in 2018 and we have already witnessed one of the top contenders in this year’s web application attacks. Continuing the trend from...
Integrate Your Ticketing System into Database Security to Prevent DBA Privilege Abuse
Many of the recent high-profile data security breaches were made by trusted insiders. They are often database administrators (DBAs) who are highly privileged and...


![A Deep Dive into Database Attacks [Part III]: Why Scarlett Johansson’s Picture Got My Postgre Database to Start Mining Monero](https://www.dataproof.co.za/wp-content/uploads/2018/03/a-deep-dive-into-database-attacks-part-iii-why-scarlett-johanssons-picture-got-my-postgre-database-to-start-mining-monero-218x150.png)