Security by Design: Why Multi-Factor Authentication Matters More Than Ever
In an era marked by escalating cyber threats and evolving risk landscapes, organisations face mounting pressure to strengthen their security posture whilst maintaining seamless...
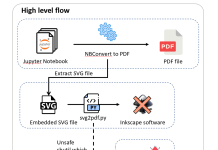
Code Execution in Jupyter Notebook Exports
After our research on Cursor, in the context of developer-ecosystem security, we turn our attention to the Jupyter ecosystem. We expose security risks we...
Imperva Partners with TollBit to Power AI Traffic Monetization for Content Owners
The surge in AI-driven traffic is transforming how websites manage their content. With AI bots and agents visiting sites at unprecedented rates (often scraping...
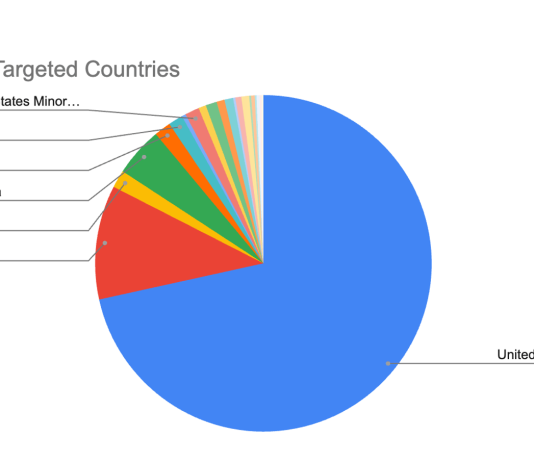
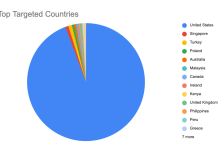
Chain Reaction: Attack Campaign Activity in the Aftermath of React Server Components Vulnerability
Introduction and Vulnerability Overview
Earlier this month, Imperva published an initial advisory outlining how our customers were protected against the newly disclosed React2Shell vulnerability impacting React Server Components (RSC). That post focused on the...
The Privacy Gap in API Security: Why Protecting APIs Shouldn’t Put Your Data at...
The more critical APIs become, the more sensitive data they carry identities, payment details, health records, customer preferences, tokens, keys, and more.
And this is...
Imperva Customers Protected Against React Server Components (RSC) Vulnerability
Overview
On December 3, 2025, the React and Next.js teams disclosed a critical security vulnerability (CVSS 10.0), identified as React2Shell, affecting applications that leverage React...
Attackers Are Quick to Exploit vBulletin’s Latest 0-day Remote Code Execution Vulnerability
Imperva’s Cloud WAF has identified instances of a new 0-day vulnerability being exploited within a matter of hours of the exploit being published.
On Monday...
A Leader in the 2019 Gartner Magic Quadrant for WAF, Six Years Running
Gartner has published its 2019 Gartner Magic Quadrant for Web Application Firewalls (WAF) and Imperva has been named a Leader for the sixth consecutive...
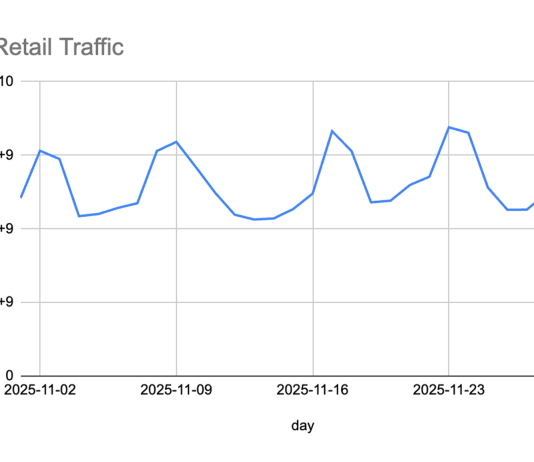
E-commerce: Bad bots are ready for the holidays. Are you?
The busiest time for online retailers is almost upon us—the holiday season. Each business is looking at ways to take advantage of cyber week...
APIs Ease Customer Interaction — and External Attacks. Here’s how to Protect Them.
To deliver seamless service experiences to our customers, businesses now rely heavily on application programming interfaces (APIs). These are a non-negotiable aspect of the...