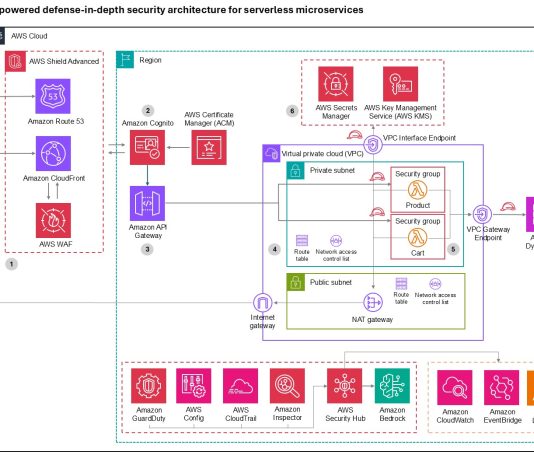
CVE-2026-20841 Windows Notepad App Remote Code Execution Vulnerability
Added an FAQ and updated the CVSS score. This is an informational change only. - Read more
Cybercrime Ethos: The Shifting Sands of Medical Neutrality
By: Josh Bartolomie, Chief Security Officer, CofenseIntroduction: A Paradigm Shift in Threat Actor BehaviorI have always told myself that I never want to become...
Fragmentation Defined 2025’s Threat Landscape. Here’s What It Means for 2026
Uncertainty has become the operating environment for business. And this year, fragmentation is driving it. The global threat landscape didn't simplify in 2025;...
State of Security Report | Recorded Future
Fragmentation is the new normal The global threat landscape didn't simplify in 2025—it shattered. Geopolitical alliances strained. Criminal enterprises splintered...
VoidLink Framework Enables On-Demand Tool Generation with Windows Plugin Support
A newly tracked intrusion framework called VoidLink is drawing attention for its modular design and focus on Linux systems. It behaves like an implant...
North Korean Hackers Use Deepfake Video Calls to Target Crypto Firms
Campaign combines stolen Telegram accounts, fake Zoom calls and ClickFix attacks to deploy infostealer malware - Read more
CVE volumes may plausibly reach 100,000 this year
The number of vulnerabilities to be disclosed in 2026 is almost certain to exceed last year's total, and may be heading towards 100,000, according...
The game is over: when “free” comes at too high a price. What we...
We often describe cases of malware distribution under the guise of game cheats and pirated software. Sometimes such methods are used to spread complex...
North Korean actors blend ClickFix with new macOS backdoors in Crypto campaign
A financially motivated threat actor tracked as UNC1609 is using a ClickFix-style social engineering campaign to deploy multiple macOS malware...