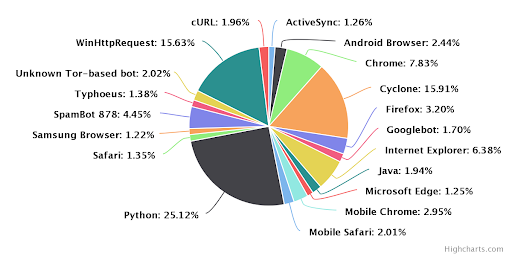
IT threat evolution Q2 2019
Targeted attacks and malware campaigns
More about ShadowHammer
In March, we published the results of our investigation into a sophisticated supply-chain attack involving the ASUS Live...
Gartner Names Centrify a Leader in Magic Quadrant for Privileged Access Management (PAM)
On December 3, 2018 Gartner released The Magic Quadrant for Privileged Access Management, Q4 2018. Evaluating 14 vendors, Gartner positioned Centrify in the LEADERS...
Financial Cyberthreats in 2018
Introduction and Key Findings
The world of finance has been a great source of income cybercriminals across the world due to an obvious reason –...
Attackers Are Quick to Exploit vBulletin’s Latest 0-day Remote Code Execution Vulnerability
Imperva’s Cloud WAF has identified instances of a new 0-day vulnerability being exploited within a matter of hours of the exploit being published.
On Monday...
A Leader in the 2019 Gartner Magic Quadrant for WAF, Six Years Running
Gartner has published its 2019 Gartner Magic Quadrant for Web Application Firewalls (WAF) and Imperva has been named a Leader for the sixth consecutive...
Roaming Mantis dabbles in mining and phishing multilingually
In April 2018, Kaspersky Lab published a blogpost titled ‘Roaming Mantis uses DNS hijacking to infect Android smartphones’. Roaming Mantis uses Android malware which...
It’s Time for Managers to Lead Security by Example, Not Blame Younger Workers
The age gap is something that all organisations over the years have had to deal with in one way or another. But the flood...
Kaspersky Security Bulletin 2018. Top security stories
Kaspersky Security Bulletin 2018. Statistics
Kaspersky Security Bulletin 2018. Story of the year: miners
Kaspersky Security Bulletin 2018. Threat Predictions for 2019
Introduction
The internet is now woven...
Ransomware: two pieces of good news
“All your files have been encrypted.” How many times has this suddenly popped up on your screen? We hope never, because it’s one of...