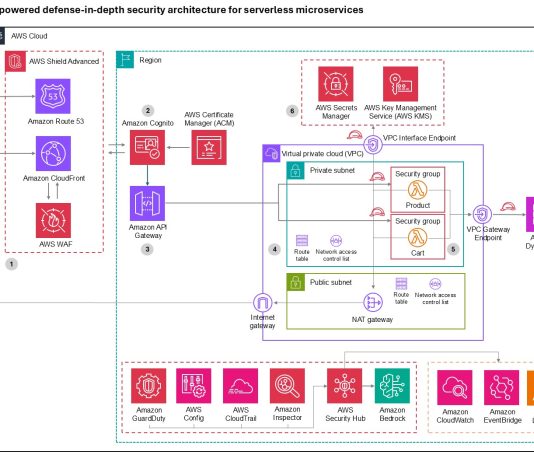
[R1] Nessus Agent Versions 11.0.4 and 11.1.2 Fix One Vulnerability
Nessus Agent Versions 11.0.4 and 11.1.2 Fix One Vulnerability Arnie Cabral Thu, 02/12/2026 - 10:40
A vulnerability has been identified where weak file...
Carding-as-a-Service: The Underground Market of Stolen Cards
Rapid7 software engineer Eliran Alon also contributed to this post.IntroductionDespite sustained efforts by the global banking and payments industry, credit card fraud continues to...
World Leaks Ransomware Group Adds Stealthy, Custom Malware ‘RustyRocket’ to Attacks
Accenture Cybersecurity warns over difficult to detect, “sophisticated toolset” being deployed as part of extortion campaigns - Read more
CISA Adds Four Known Exploited Vulnerabilities to Catalog
CISA has added four new vulnerabilities to its Known Exploited Vulnerabilities (KEV) Catalog, based on evidence of active exploitation.
CVE-2024-43468 Microsoft Configuration Manager SQL Injection...
Siemens SINEC OS
View CSAF
Summary
SINEC OS before V3.3 contains third-party components with multiple vulnerabilities. Siemens has released new versions for the affected products and recommends to update...
Siemens Siveillance Video Management Servers
View CSAF
Summary
The Webhooks implementation of Siveillance Video Management Servers contains a vulnerability that could allow an authenticated remote attacker with read-only privileges to achieve...
Siemens Solid Edge
View CSAF
Summary
Solid Edge uses PS/IGES Parasolid Translator Component that contains an out of bounds read that could be triggered when the application reads files...
Siemens SINEC NMS
View CSAF
Summary
Multiple Siemens products are affected by two local privilege escalation vulnerabilities which could allow an low privileged attacker to load malicious DLLs, potentially...
Ryan Liles, master of technical diplomacy
Cisco Talos is back with another inside look at the people who keep the internet safe. This time, Amy chats with Ryan Liles, who...
How to build an incident response framework
Frameworks provide the structure for an effective incident response program. Here's where to turn for guidance on what to include. - Read more