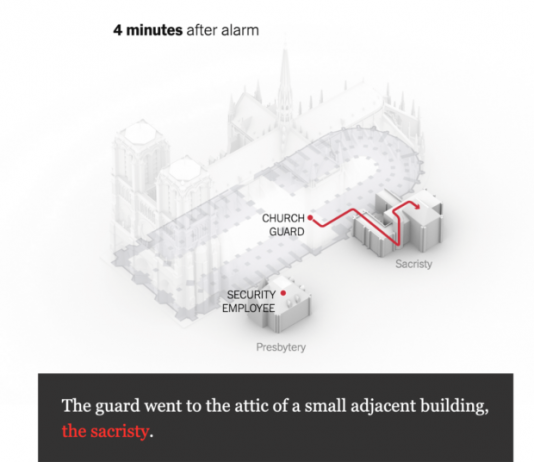
Zero Trust Lessons from a Holiday Classic
Every year when the holidays roll around, I’m amazed at the way shopping deals dominate the headlines. Black Friday and Cyber Monday are annual...
Gartner Names Centrify a Leader in Magic Quadrant for Privileged Access Management (PAM)
On December 3, 2018 Gartner released The Magic Quadrant for Privileged Access Management, Q4 2018. Evaluating 14 vendors, Gartner positioned Centrify in the LEADERS...
Forrester Names Centrify a Leader in Privileged Identity Management
Today Forrester Research released The Forrester Wave: Privileged Identity Management, Q4 20181. Evaluating 11 vendors, Forrester named Centrify a Leader.
Here at Centrify, we believe this...
The Base of Cyber-Attacks: Credential Harvesting
Cyber attackers long ago figured out that the easiest way to gain access to sensitive data is by compromising an end user’s identity and...
Centrify’s new spinout, Idaptive, named Overall Leader in KuppingerCole Leadership Compass for Cloud-based MFA...
Wow! Right out of the gate and the brand new spinout of Centrify Application and Endpoint Services as Idaptive is named as an Overall...
At SecurIT in New York, it’s a Zero Trust State of Mind
On October 29-30, Centrify will proudly sponsor the second SecurIT: the Zero Trust Summit for CIOs and CISOs in New York City. Produced by...
Moving Beyond Legacy PAM: Centrify Zero Trust Privilege
Our customers trust us to keep their most privileged credentials – the “keys to the kingdom” – secure from being exploited. Over half of...
Stay Secure with Day-One Support for iOS 12 and macOS Mojave
It’s that time of year again: time for all the latest and greatest from our friends in Apple Park (or the Apple Spaceship as...
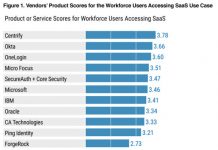
Centrify Scores Highest for Both “Workforce Users Accessing SaaS” and “Business-to-Business” in New Gartner...
Gartner just released their first ever “Critical Capabilities for Access Management, Worldwide, 2018” report, and we are proud to see that Centrify has scored...
Behind the Numbers: Database Authentication and Authorization
Earlier this month, I posted a blog about how most companies I speak with have not implemented a modern database authentication and authorization approach....