How to Authenticate Users Into Apps Using AWS Application Load Balancer and Centrify
At Centrify, an AWS Partner Network (APN) Advanced Technology Partner, we frequently work with developers building applications on Amazon Web Services (AWS). While many aspects of app...
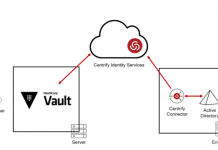
Introducing Centrify Identity Services for HashiCorp Vault
Today, Centrify is proud to announce the integration of the Centrify Identity Service with HashiCorp Vault for role-based user authentication and access to the...
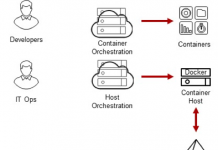
Centrify Identity Services: Securing Docker and Containers
Introduction
We are excited to announce that Centrify now supports CoreOS Container Optimized Linux which several of our customers are using as part of their...
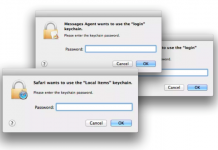
Sync Your Jaws Into Mac Keychain
“Well this is not a boat accident! It wasn’t any propeller! It wasn’t any coral reef! And it wasn’t Jack the Ripper! It was...
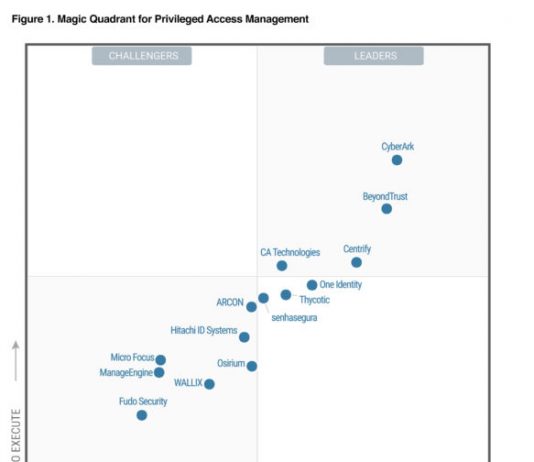
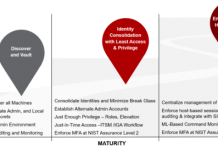
Gartner Names PAM a Top Security Project (AGAIN!) in 2019
Last June at the 2018 Gartner Security & Risk Management Summit, the analyst firm issued a “Smarter with Gartner” paper outlining the Top 10...
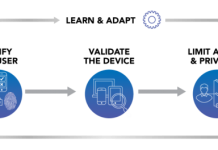
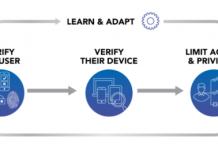
How to Operationalize the Zero Trust Security Pillar ‘Limit Access & Privilege’ with ServiceNow
An easy way for a cyber-attacker to gain access to sensitive data is by compromising an end user’s identity and credentials. Things get even...
World Password Day – 5 Facts About Weak Credentials
Happy World Password Day!
Ok, I’ll admit until a few days ago, I wasn’t aware this was a thing. As with most events in my...
Adopt Next-Gen Access to Power Your Zero Trust Strategy
Security breaches are now all too commonplace — 58% of organizations have experienced at least one in the past 12 months. As a result,...
Stop Breaches with Analytics and Artificial Intelligence
According to Gartner, companies will spend up to $96 billion worldwide on security this year, but research by Centrify and Dow Jones suggests that...
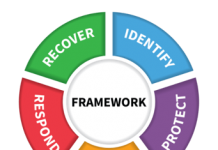
Five Best Practices for Zero Trust Security
The Centrify Zero Trust Security model is effective because it allows organizations to remove trust from the equation entirely. Based on the assumption that...