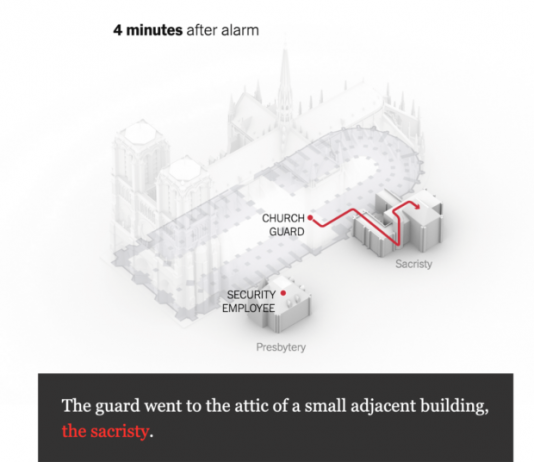
Top 3 PAM Features that Set Centrify Zero Trust Privilege Apart for Cloud Migrations
Ask any sales person what the most common question they get from prospects is, and the answer will typically be the same: “What makes...
Centrify Mid-Year Data Breach Report: Credential Abuse One of the Top Threats of Cyber...
It’s hard to believe that we’re already more than halfway through 2019. Or as I like to put it, I’ve already wasted one month...
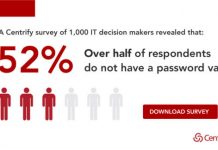
52% of Companies Don’t have a Password Vault for Privileged Access – Here’s Your...
Over the first half of 2019, Centrify issued two research reports about the adoption of Privileged Access Management (PAM) solutions and the maturity of...
Centrify Closes Out a Busy June at AWS Re:Inforce and Identiverse
June has been a busy month in the cybersecurity space! It started off with InfoSec Europe and SailPoint Navigate, next week we’ll wrap up...
Minimizing Exposure to Ransomware Attacks with Centrify Zero Trust Privilege
Ransomware attacks like the ones that wreaked havoc in Baltimore, Maryland, Albany, New York, and Genesee County, Michigan are dominating the headlines in 2019....
New Centrify Report: Stop Putting Up with Bad Karaoke and Start Learning about Zero...
You know when you’re hanging out with friends, maybe doing a little drinking, and somebody suggests that you go to a karaoke bar? “Heck...
NASCIO CIO Top Priorities in a Zero Trust World
Many state CIOs are struggling to manage the onslaught of priorities that are captured in the NASCIO Top 10 Policy and Technology Priorities for...
Centrify Achieves FedRAMP Authorization
Centrify received exciting news this week that we are now FedRAMP Authorized!
For those who don’t know about FedRAMP, it is a government-wide program that...
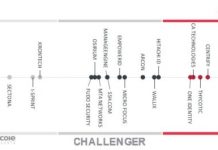
3 for 3! Centrify a Leader in 2019 KuppingerCole Leadership Compass for PAM
KuppingerCole recently published its 2019 KuppingerCole Leadership Compass for Privileged Access Management (PAM), again recognizing Centrify as a Leader as it did in the...
Centrify Empowers Our Partners to Unleash P.E.A.K. Performance
I’m thrilled today to debut Centrify P.E.A.K. Performance, our new partner program!
This launch is the culmination of a long period of listening. We’ve spent...