Why the Path Towards Zero Trust Starts with Next-Gen Access
Zero Trust Security has gained a lot of popularity over the last six months. Almost daily you can read articles about this security strategy...
Pocket cryptofarms
In recent months, the topic of cryptocurrency has been a permanent news fixture — the value of digital money has been see-sawing spectacularly. Such...
GDPR and Privacy: How to Earn the Trust of Your Customers and Keep Regulators...
Customer data is the lifeblood of any organisation and the key to unlocking sales and growth. But the data you hold and how you...
Your new friend, KLara
While doing threat research, teams need a lot of tools and systems to aid their hunting efforts – from systems storing Passive DNS data...
Real-Life Exposed Privileged Identity Theft
Have you ever had your identity stolen? Credit cards obtained under your name that were not yours?
Most of us have, and what a pain...
Threat Landscape for Industrial Automation Systems in H2 2017
For many years, Kaspersky Lab experts have been uncovering and researching cyberthreats that target a variety of information systems – those of commercial and...
Six Reasons to Experience Zero Trust Security in Centrify Booth 501 at RSA
In case you hadn’t heard, the 2018 RSA Conference will be held April 16-19 at the Moscone Center in San Francisco. If you haven’t...
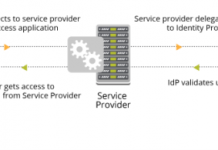
Making Headlines: SAML
On February 27, 2018 the CERT Division of Carnegie Mellon University’s Software Engineering Institute issued advisory #475445, outlining a design flaw in Security Assertion...
Goodfellas, the Brazilian carding scene is after you
There are three ways of doing things in the malware business: the right way, the wrong way and the way Brazilians do it. From...