A Ticking Time Bomb: Understanding and Securing the Next Generation of Workers
It’s sometimes easy to forget that the younger employees of today are the managers of tomorrow. If we fail to understand how they use...
It’s Time for Managers to Lead Security by Example, Not Blame Younger Workers
The age gap is something that all organisations over the years have had to deal with in one way or another. But the flood...
Ransomware and malicious crypto miners in 2016-2018
Ransomware is not an unfamiliar threat. For the last few years it has been affecting the world of cybersecurity, infecting and blocking access to...
Black Hat 2018
<img src="/sites/default/files/Blackhat-logo.png">
Join Digital Guardian at Black Hat 2018!
- Read more
Making Smarter Access Control Decisions
Hey Siri, block that attacker, please
Wouldn’t it be great if Siri, Alexa, or Google Assistant had the intelligence to figure out malicious intent, govern...
Pbot: evolving adware
The adware PBot (PythonBot) got its name because its core modules are written in Python. It was more than a year ago that we...
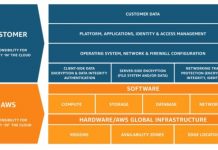
Zero Trust Security and DevOps Take the Crown at AWS Public Sector Summit 2018
Last week, Amazon Web Services hosted its AWS Public Sector Summit in Washington, DC. In its 9th year, the event attracted thousands of global...
Cyber Risk Insights from the AIG 2017 Cyber Insurance Review
I read with interest AIG’s 2017 Cyber Insurance Review. In a one sentence summary: cyber insurance claims are up, due to systemic ransomware and...
Centrify Named a Visionary in the 2018 Magic Quadrant for Access Management, Worldwide
Download the 2018 Gartner Magic Quadrant for Access Management
Centrify has been named a Visionary by Gartner, Inc. in the 2018 Magic Quadrant for Access...