We recently saw a new DDoS amplification attack vector via memcached servers that culminated in two massive DDoS amplification attacks on February 28. Both attacks were mitigated successfully.
Here’s how memchached servers work and how the attacks unfolded.
Memcached servers
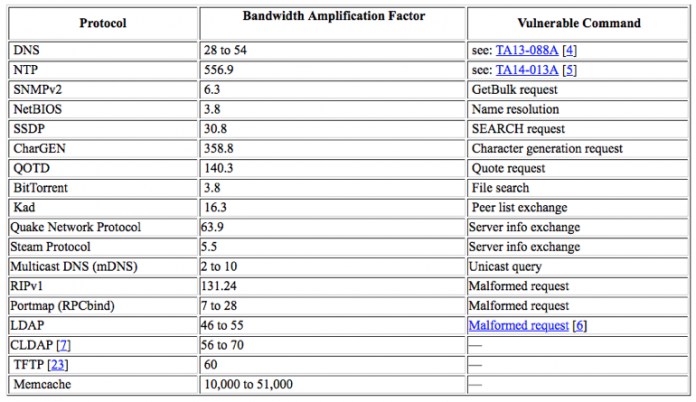
Unless updated within the last two days, memcached servers listen on UDP port 11211 by default. This can be exploited to produce DDoS amplification attacks by sending the memcached server a UDP packet with a spoofed IP containing a message asking for statistics, which will cause the server to return an enormous message to the victim. Exploitable DDoS amplification vectors allow attackers to deliver massive and/or many packets for each small packet they send, without the need to control a botnet of hacked devices. Amplification attacks via memcached servers result in an amplification factor of 9,000 X or more. As a comparison, NTP, a DDoS amplification vector known for its high amplification factor typically reaches an amplification factor of 557 X the original payload.

Credit: US-CERT, https://www.us-cert.gov/ncas/alerts/TA14-017A
Total number of memcached servers globally
There are over 93,000 memcached servers listening on port 11211 all over the world, allowing attackers to choose from a variety of servers and avoid having their IP blacklisted.
The beginnings of a new attack vector
We started seeing a number of DDoS attacks using this method in the last few days. The first attack hit the network on February 21 with another attack launching on February 26 that reached 190 Gbps and 18Mpps and lasted over an hour.
On February 28 we saw the following attacks.
Detecting and mitigating an attack on memcached servers
Although the attack can be easily detected by setting a rule on UDP traffic coming from source port 11211, it cannot be mitigated without a dedicated DDoS mitigation solution due to the massive amounts of PPS and BPS delivered on such an attack, which are likely to turn edge routing devices unavailable before traffic arrives at the server, regardless of its configuration.
Imperva Incapsula Infrastructure customers are protected against all known DDoS amplification attacks, and as of now they are protected against this specific attack as well.