Protecting Your Organization from the Next Big Ransomware Threat
Protecting Your Organization from the Next Big Ransomware Threat #outlook a{ padding:0;...
Welcome to The State of Security
Welcome to The State of Security #outlook a{ padding:0; } body{ width:100%...
Hunting for Insider Threats: Using Activity Modeling to Detect Suspicious Database Commands and Access...
The Widening Gap
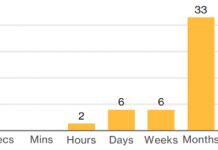
Data breaches by insiders are very challenging to catch. The gap between the rise of insider threats and speed of hunting them...
With Less Than 100 Days to Go, How to Get C-Level Buy-in for GDPR...
For GDPR compliance initiatives to work effectively, there has to be buy-in from the boardroom. That doesn’t just mean releasing the necessary funds to...
Another Ransomware Variant Strikes Colorado DOT Days after Initial Attack
Posts from The State of Security for 03/02/2018
Inside a New DDoS Amplification Attack Vector via Memcached Servers
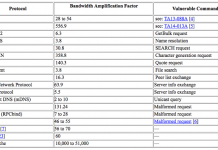
We recently saw a new DDoS amplification attack vector via memcached servers that culminated in two massive DDoS amplification attacks on February 28. Both...
Takeaways from the Russia-Linked US Senate Phishing Attacks
The Zero Trust Security approach could empower organizations and protect their customers in ways that go far beyond typical security concerns.
On January 12, 2018,...
Financial Cyberthreats in 2017
In 2017, we saw a number of changes to the world of financial threats and new actors emerging. As we have previously noted, fraud...
IoT hack: how to break a smart home… again
There can never be too many IoT gadgets – that’s what people usually think when buying yet another connected device with advanced functionality. From...
Multi-factor Authentication (MFA) Is Ready for Prime Time
We’ve heard it time and again. As security threats increase and morph, and user devices and locations diversify, multi-factor authentication (MFA) should be blossoming...