It’s Almost GDPR D-Day: So What Happens Next?
Over the past 12 months during this blog series I’ve tried to provide insight into some of the key aspects of the GDPR and...
Backdoors in D-Link’s backyard
“If you want to change the world, start with yourself.” In the case of security research this can be rephrased to: “If you want...
Threat Prevention is Foundational
Threat Prevention is Foundational #outlook a{ padding:0; } body{ width:100% !important; }...
Centrify Does it Again – Innovative Security Analytics Integration with Palo Alto Networks App...
Centrify and Palo Alto Networks have announced another important integration that can help customers quickly and decisively discover anomalies that are a security threat.
Building...
Facebook, GDPR and the Right to Privacy: Three’s a Crowd?
Back in 2016 the European Union voted to pass the mother of all security laws, aimed at further extending the rights of its citizens...
Roaming Mantis dabbles in mining and phishing multilingually
In April 2018, Kaspersky Lab published a blogpost titled ‘Roaming Mantis uses DNS hijacking to infect Android smartphones’. Roaming Mantis uses Android malware which...
Analyst Insights – Building An Efficient Data Security Program with Forrester
Analyst Insights – Building An Efficient Data Security Program
This webinar was recorded on May 17, 2018.
- Read more
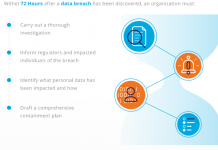
72 Hours: Understanding the GDPR Data Breach Reporting Timeline
We’re down to the wire with respect to the General Data Protection Regulation (GDPR) compliance deadline of May 25, 2018.
Organizations that fail to comply...
Electronic Health Record Systems Under Attack
Electronic Health Record Systems Under Attack #outlook a{ padding:0; } body{ width:100%...









![[VitalQIP Migration Series] Part 1: Three Reasons Why VitalQIP Migration Should Be on Your Radar](http://www.dataproof.co.za/wp-content/uploads/2018/05/vitalqip-migration-series-part-1-three-reasons-why-vitalqip-migration-should-be-on-your-radar-218x150.jpg)










