Survey: 44% of Security Professionals Spend More than 20 Hours a Week Responding to...
As the global cybersecurity climate continues to heat up, so too do the subsequent levels of alert fatigue IT security professionals have to deal...
Defense in Depth: 4 Essential Layers of ICS Security
Defense in Depth: 4 Essential Layers of ICS Security #outlook a{ padding:0;...
Octopus-infested seas of Central Asia
For the last two years we have been monitoring a Russian-language cyberespionage actor that focuses on Central Asian users and diplomatic entities. We named...
Threats in the Netherlands
Introduction
On October 4, 2018, the MIVD held a press conference about an intercepted cyberattack on the OPWC in the Netherlands, allegedly by the advanced...
MuddyWater expands operations
Summary
MuddyWater is a relatively new APT that surfaced in 2017. It has focused mainly on governmental targets in Iraq and Saudi Arabia, according to...
Zero-day exploit (CVE-2018-8453) used in targeted attacks
Yesterday, Microsoft published their security bulletin, which patches CVE-2018-8453, among others. It is a vulnerability in win32k.sys discovered by Kaspersky Lab in August. We...
Is it time to fire your vulnerability management provider?
Is it time to fire your vulnerability management provider? #outlook a{ padding:0;...
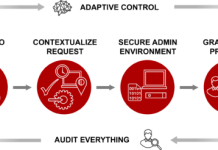
Moving Beyond Legacy PAM: Centrify Zero Trust Privilege
Our customers trust us to keep their most privileged credentials – the “keys to the kingdom” – secure from being exploited. Over half of...