A predatory tale: Who’s afraid of the thief?
In mid-February, Kaspersky Lab received a request for incident response from one of its clients. The individual who initially reported the issue to our...
Friday Five: 3/8 Edition
Your Email Title
[Case Study] Preventing Information Security Silos
Tripwire, Inc.
Mapping Communication Between Facebook Accounts Using a Browser-Based Side Channel Attack
A now-patched vulnerability in the web version of Facebook Messenger allowed any website to expose who you have been messaging with.
In a previous post,...
Financial Cyberthreats in 2018
Introduction and Key Findings
The world of finance has been a great source of income cybercriminals across the world due to an obvious reason –...
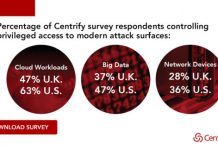
Time to Retire “The Year Of…” at RSA 2019
Today at the RSA Security Conference, we announced Centrify’s Cloud-Ready Zero Trust Privilege Services architecture, including a wide range of enhancements that redefine legacy...
Case Study: Keeping the Lights On with NERC CIP Compliance from Tripwire
Case Study: Keeping the Lights On with NERC CIP Compliance from Tripwire ...
Hundreds of Vulnerable Docker Hosts Exploited by Cryptocurrency Miners
Docker is a technology that allows you to perform operating system level virtualization. An incredible number of companies and production hosts are running Docker...
Centrify RSA Booth 6445: Where Zero Trust Privilege Partners Take the Stage
If there was one clear takeaway from the 2018 RSA Conference, it was that Zero Trust was ready to take off.
It seemed like everywhere...






![[Case Study] Preventing Information Security Silos](http://www.dataproof.co.za/wp-content/uploads/2019/03/case-study-preventing-information-security-silos.jpg)