Today at the RSA Security Conference, we announced Centrify’s Cloud-Ready Zero Trust Privilege Services architecture, including a wide range of enhancements that redefine legacy Privileged Access Management (PAM). If you are at the show, we hope you pay us a visit in Booth 6445 where we can demo a range of DevOps, Automation, hybrid cloud, and infrastructure security protections for PAM.
I’ve been going to RSA on and off for 22 years. Of course, the show is quite a different beast now. In 1997, the show was hosted for the first time at the Fairmont Hotel in San Francisco. It was still a relatively intimate affair, with ~300 attendees, and a general mix of vendors as well as deeply technical audience in the practice and R&D of what you could call “pure” cryptography (algorithms and mathematical proofs).
Today, that deeply technical audience still comes to RSA, but around them it has exploded with 50,000 attendees. And with them, every year a pronounced new technology wave.
In fact, a veritable guessing game springs up every year for RSA show walkers: ”It really felt like the year of…” and insert your technology trend through the years. ”The Year of Internet security startups”, the year of firewall vendors, mobile security, the year of PKI, several years of the smartcard (Boston’s Security Dynamics the SecurID token company bought San Mateo’s RSA the crypto company on this bet in 1996), the year of NAC, the year of next generation SIEM, to today’s newest waves of cloud security, SaaS security and CASB, automation and AI, intention based security, and more to come.
But through all of that innovation, market expansion, technical evolution, maybe it’s time to lose “Year Of” thinking? After all, the “bad guys” seem to have as much success in The Year Of… the VPN, smartcard, mobile, NAC, SIEM, CASB, AI, etc. And while there is robust agreement that a PAM strategy is fundamental to IT security (https://blog.centrify.com/gartner-pam-top-security-project-2019/), project ranking is probably not enough.
In a world where enterprise IT organizations are forced to move faster and faster, I don’t think it’s the next new technology that matters. I think it’s about the speed at which you can deploy any technology. Deploy and get value from it. Call it your mean-time-to-value score. That’s where I think the industry should focus. It’s not shiny new things, it’s deploying them in a pragmatic and practical way.
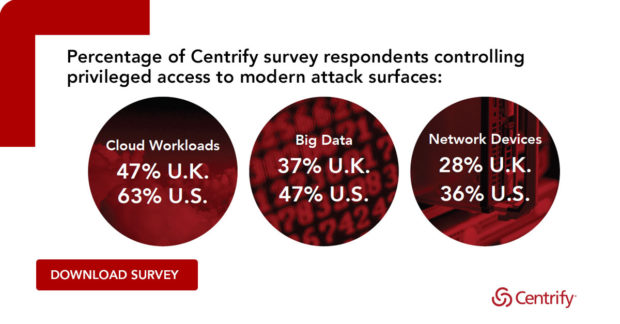
Our recent survey of 1,000 IT decision makers revealed that most organizations are not even doing some of the basics when it comes to Privileged Access Management. 52% don’t even have a password vault. But what’s interesting is the reasons why they are not doing the basics: it mainly comes down to budget and executive buy-in, not difficulty or priority.
So it’s not a surprise, then, that they are also not securing most of the emerging modern attack surfaces that hackers are seeking to exploit, such as cloud infrastructure, Big Data, DevOps and more.
And that’s where the power of Centrify’s cloud-ready Zero Trust Privilege Services lies. Quite simply, across the places where you should consider limiting, reducing, or deploying just-in-time, just enough privilege, there is no easier, or faster way to reduce your mean-time-to-value.
Some proof points:
#1. 10 Mins to PAM. Fire up our free trial. More respondents in our survey said the desire to adhere to best practices was driving the decision on how to implement PAM at their organizations, not simply compliance. So get busy doing! As a SaaS cloud, we can provision you a full PAM cloud-based solution in the time it took to read this blog: https://www.centrify.com/free-trial/
#2. Not quite ready to jump in? These videos are short and quick and have practical value around quick steps you should take to improve your Privilege Security posture.
- Need a fast and easy way to manage admin access in Public Clouds? Start here
- How about a repeatable, manageable way to discover (and import) resources and privileged users into PAM. Video here.
- Lastly, modern DevOps applications often need to embed secrets and access to keys, this demo illustrates how Centrify Zero Trust Privilege Services application password management mitigates the risks associated with cyber attackers trolling through scripts, application code and configuration files on servers looking for embedded credentials. Demo here:
#3. Seeing is believing, but so is meeting the experts. If you’d like to network with colleagues as well as get hands-on test drives via Cloudshare to learn how you can protect your privilege access from breach, we’re coming to 5 cities in March – view the full list of events here: https://www.centrify.com/lp/test-drive-roadshow-2019/
The post Time to Retire “The Year Of…” at RSA 2019 appeared first on Secure Thinking by Centrify.