Take these Five Steps to Really Mitigate your Data Breach Risks
Data breaches are a CSO/CISO’s worst nightmare. And they’re getting bigger and more damaging all the time. It’s no longer just hundreds of millions...
The 2019 DBIR is out
Once again, we are happy to support a large, voluntary, collaborative effort like the 2019 Data Breach Investigations Report. While our data contribution is...
FIN7.5: the infamous cybercrime rig “FIN7” continues its activities
On August 1, 2018, the US Department of Justice announced that it had arrested several individuals suspected of having ties to the FIN7 cybercrime...
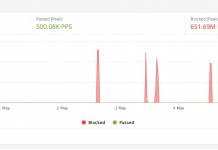
Botnet-led DDoS Attacks Are Hitting Record Intensities. Imperva is Mitigating All of Them.
DDoS attacks are usually ranked by the amount of bandwidth involved, such as the 2018 GitHub attack that peaked at 1.35 Terabits per second...
Calculating the ROI of a Vulnerability Management Program
Calculating the ROI of a Vulnerability Management Program #outlook a{ padding:0; }...
[Buyer’s Guide] DevOps Security
Tripwire, Inc.
NASCIO CIO Top Priorities in a Zero Trust World
Many state CIOs are struggling to manage the onslaught of priorities that are captured in the NASCIO Top 10 Policy and Technology Priorities for...
Building a Mature Vulnerability Management Program
Building a Mature Vulnerability Management Program #outlook a{ padding:0; } body{ width:100%...







![[Buyer’s Guide] DevOps Security](http://www.dataproof.co.za/wp-content/uploads/2019/05/buyers-guide-devops-security.jpg)












