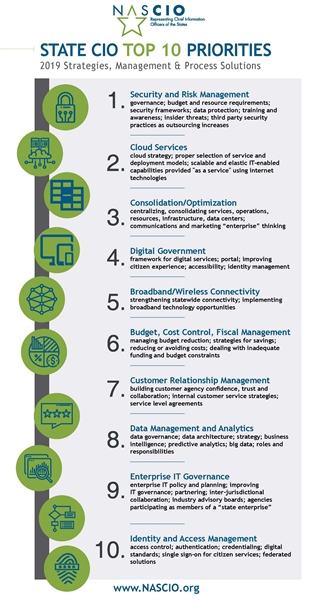
Many state CIOs are struggling to manage the onslaught of priorities that are captured in the NASCIO Top 10 Policy and Technology Priorities for 2019, ranging from enabling cloud services to the digital government to IT governance. While their mission mandates tackling these priorities, they cannot solely focus on their implementation, but must also bolster cyber security and abide by stringent compliance mandates (e.g., FISMA, HIPAA, NIST SP 800-Series). This is a tall order to deal with.
To add to this challenge, the attack surface of state governments has changed dramatically. Today state agencies must not only control access to servers, databases, and network devices, but also look after cloud environments. At the same time, it’s become evident that attackers are no longer “hacking” to carry out data breaches ― they are simply logging in by exploiting weak, stolen, or otherwise compromised privileged credentials. According to Forrester estimates, 80 percent of today’s breaches involve privileged credential misuse.

Think Zero Trust ― For All Initiatives
It’s just further proof that we’re living in a World of Zero Trust, which mandates state CIOs to apply a new mindset of “never trust, always verify, enforce least privilege.” In this context, next-generation solutions like Zero Trust Privilege are a necessity to secure state governments while supporting the breadth of initiatives described in the NASCIO Top Priorities list.
Let’s look at how Zero Trust Privilege can serve as the overarching umbrella for these initiatives:
#1: Security & Risk Management
Increase your compliance and security posture by addressing today’s leading cause of breaches — privileged access abuse. Grant least privilege access based on verifying who is requesting access, the context of the request, and the risk of the access environment.
#2: Cloud Services
Adopt cloud seamlessly and securely — simply extend your existing enterprise identities and multi-factor authentication (MFA) to your hybrid cloud.
#3: Consolidation/Optimization
Reduce vendor sprawl: Zero Trust Privilege combines password vaulting with brokering of identities, MFA enforcement, and “just enough” privilege, all while securing remote access and monitoring all privileged access sessions.
#4: Digital Government
Secure and streamline access to all infrastructure elements — on-premise, cloud, or hybrid.
#5: Broadband/Wireless Connectivity
Secure, streamline, and audit administrative access to network devices.
#6: Budget, Cost Control, Fiscal Management
Save implementation and operational costs by applying a Zero Trust Privilege approach.
#7: Customer Relationship Management
Improve citizen trust by minimizing the risk of data exfiltration.
#8: Data Management & Analytics
Take advantage of machine learning to discover risky privileged user behavior and apply conditional access.
#9: Enterprise IT Governance
Govern, approve, provision, remove, and report on privileged access.
#10: Identity and Access Management
Streamline, secure, and protect privileged access to critical resources.
Your mission is evolving, regulations are evolving, and the threatscape is evolving too. Thus, “trust but verify” is no longer a valid approach. The Zero Trust framework provides CIOs and security leaders a rigorous approach to defend and counter today’s escalating risk, while empowering their high priority initiatives.
The post NASCIO CIO Top Priorities in a Zero Trust World appeared first on Secure Thinking by Centrify.