Secure Identity to Protect Your Reputation
Reputation is built on trust – yet the paradox in the age of access is that the only way we can build trust is...
Centrify’s Next Strategic Step Forward with Thoma Bravo
I am pleased as CEO and co-founder of Centrify to announce that Centrify has entered into a definitive agreement whereby Thoma Bravo, a leading...
A Ticking Time Bomb: Understanding and Securing the Next Generation of Workers
It’s sometimes easy to forget that the younger employees of today are the managers of tomorrow. If we fail to understand how they use...
It’s Time for Managers to Lead Security by Example, Not Blame Younger Workers
The age gap is something that all organisations over the years have had to deal with in one way or another. But the flood...
Making Smarter Access Control Decisions
Hey Siri, block that attacker, please
Wouldn’t it be great if Siri, Alexa, or Google Assistant had the intelligence to figure out malicious intent, govern...
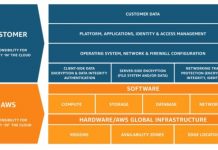
Zero Trust Security and DevOps Take the Crown at AWS Public Sector Summit 2018
Last week, Amazon Web Services hosted its AWS Public Sector Summit in Washington, DC. In its 9th year, the event attracted thousands of global...
Cyber Risk Insights from the AIG 2017 Cyber Insurance Review
I read with interest AIG’s 2017 Cyber Insurance Review. In a one sentence summary: cyber insurance claims are up, due to systemic ransomware and...
Centrify Named a Visionary in the 2018 Magic Quadrant for Access Management, Worldwide
Download the 2018 Gartner Magic Quadrant for Access Management
Centrify has been named a Visionary by Gartner, Inc. in the 2018 Magic Quadrant for Access...
Identity-Based Security Comes of Age at Infosec18
The annual Infosecurity Europe (Infosec) show was back again at the start of June even bigger and better than before. This year it was...
LIVE BLOG: SecurIT Zero Trust Summit
REGISTER BELOW FOR THE LIVE STREAM!
Welcome to the live blog from SecurIT: the Zero Trust Summit for CIOs and CISOs.
SecurIT is an all-day...