World Password Day – 5 Facts About Weak Credentials
Happy World Password Day!
Ok, I’ll admit until a few days ago, I wasn’t aware this was a thing. As with most events in my...
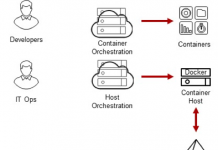
Centrify Identity Services: Securing Docker and Containers
Introduction
We are excited to announce that Centrify now supports CoreOS Container Optimized Linux which several of our customers are using as part of their...
Centrify Booth 2410: Your Destination for All Things Zero Trust Security at BlackHat USA
BlackHat USA 2018 kicks off in Las Vegas next week, the 21st year that the information security event has brought together thousands of cybersecurity...
Centrify Launches Zero Trust Security Network Ecosystem
The world has changed. I’m not sure if it was the HBO breach, Equifax, Yahoo, or one of the many breaches since, but after...
Centrify Predicts: Cybersecurity in 2018
As we start 2018, we have continued to see major breaches across industries, only last year we witnessed at least two companies — Uber...
New Centrify Report: Stop Putting Up with Bad Karaoke and Start Learning about Zero...
You know when you’re hanging out with friends, maybe doing a little drinking, and somebody suggests that you go to a karaoke bar? “Heck...
Secure Identity to Protect Your Reputation
Reputation is built on trust – yet the paradox in the age of access is that the only way we can build trust is...
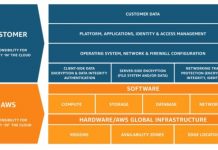
Zero Trust Security and DevOps Take the Crown at AWS Public Sector Summit 2018
Last week, Amazon Web Services hosted its AWS Public Sector Summit in Washington, DC. In its 9th year, the event attracted thousands of global...
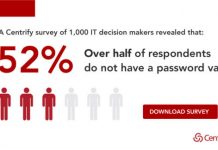
52% of Companies Don’t have a Password Vault for Privileged Access – Here’s Your...
Over the first half of 2019, Centrify issued two research reports about the adoption of Privileged Access Management (PAM) solutions and the maturity of...
Multi-factor Authentication (MFA) Is Ready for Prime Time
We’ve heard it time and again. As security threats increase and morph, and user devices and locations diversify, multi-factor authentication (MFA) should be blossoming...