The Year in Review: Rethink Security
During a year of high-profile breaches like Equifax, HBO and Uber, as well as the realization that Yahoo’s highly-publicized 2013 breach compromised the accounts...
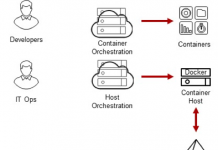
Centrify Identity Services: Securing Docker and Containers
Introduction
We are excited to announce that Centrify now supports CoreOS Container Optimized Linux which several of our customers are using as part of their...
GUEST BLOG: A Gen Z’s Perspective on Cybersecurity
I had the pleasure to mentor a summer intern named Min Ji Kim, who is returning to NYU to continue her education next week....
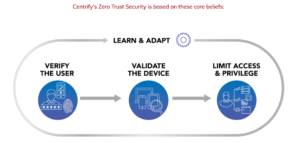
Centrify Launches Zero Trust Security Network Ecosystem
The world has changed. I’m not sure if it was the HBO breach, Equifax, Yahoo, or one of the many breaches since, but after...
Trends to look for next week at RSA Conference 2018
Next week (April 16-19) is the 2018 RSA Conference at the Moscone Center in San Francisco, and there’s good news: it’s not too late...
C-Suite Disconnect is Weakening Cybersecurity
Today, Centrify announced a new research study conducted with Dow Jones Customer Intelligence titled, “CEO Disconnect is Weakening Cybersecurity.” The report sheds light on...
A Ticking Time Bomb: Understanding and Securing the Next Generation of Workers
It’s sometimes easy to forget that the younger employees of today are the managers of tomorrow. If we fail to understand how they use...
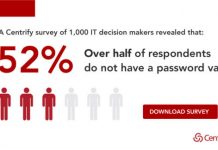
52% of Companies Don’t have a Password Vault for Privileged Access – Here’s Your...
Over the first half of 2019, Centrify issued two research reports about the adoption of Privileged Access Management (PAM) solutions and the maturity of...
451 Research: Centrify Goes “All In” on the Zero Trust Movement
451 Research recently published an impact report recognizing Centrify as one of the early vendors to embrace the Zero Trust concept, which is a...
The State of Cyber Security in Healthcare
The privacy and security concerns associated with digital patient records make the healthcare industry one of the most regulated industries in the United States....