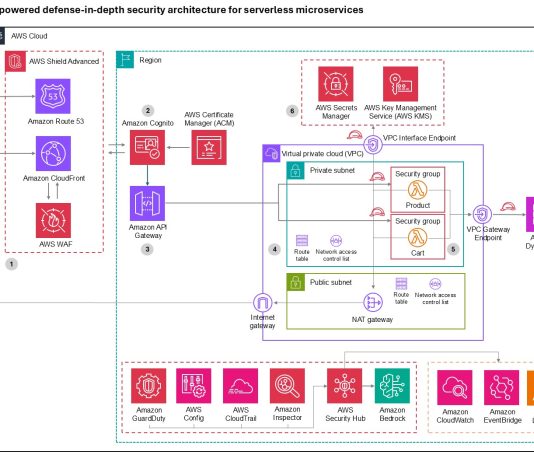
Kaspersky Security Bulletin. Overall statistics for 2017
All the statistics used in this report were obtained using Kaspersky Security Network (KSN), a distributed antivirus network that works with various anti-malware protection components....
Still Stealing
Two years ago in October 2015 we published a blogpost about a popular malware that was being distributed from the Google Play Store. Over...
Cybercriminals vs financial institutions in 2018: what to expect
ul li {margin-bottom:2.4rem;}
Introduction – key events in 2017
2017 was a year of great changes in the world of cyberthreats facing financial organizations.
Firstly, in 2017...
Kaspersky Security Bulletin: Review of the Year 2017
ul li {margin-bottom:2.4rem;}
Introduction
The end of the year is a good time to take stock of the main cyberthreat incidents that took place over the...
Kaspersky Security Bulletin: Story of the year 2017
Download the Kaspersky Security Bulletin: Story of the year 2017
Introduction: what we learned in 2017
In 2017, the ransomware threat suddenly and spectacularly evolved. Three...
IoT lottery: finding a perfectly secure connected device
Black Friday and Cyber Monday are great for shopping. Vendors flood the market with all kinds of goods, including lots of exciting connected devices...