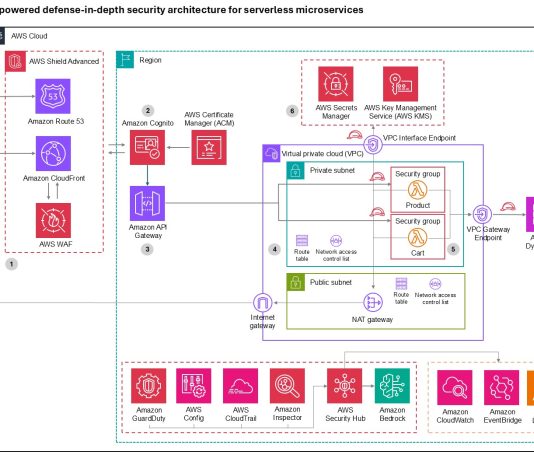
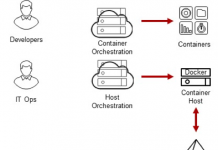
Centrify Identity Services: Securing Docker and Containers
Introduction
We are excited to announce that Centrify now supports CoreOS Container Optimized Linux which several of our customers are using as part of their...
4 Steps to Reduce the Risk of Shared Account Passwords
Reduce the Risk of a Security Breach When Sharing Privileged Accounts
There are partners, employees, contractors, customers and others who access or try to access...
KLAS Findings on Healthcare DLP Strategies
KLAS Findings on Healthcare DLP Strategies
This webinar was recorded on December 19, 2017.
- Read more
Centrify Predicts: Cybersecurity in 2018
As we start 2018, we have continued to see major breaches across industries, only last year we witnessed at least two companies — Uber...
The Year in Review: Centrify Builds Momentum
The Centrify solution made great strides in 2017, chronicled in Part I of this blog. Product enhancements, combined with the market’s growing understanding of...
Happy IR in the New Year!
At the end of last year Mr. Jake Williams from aka @MalwareJake asked a very important question about Lack of visibility during detecting APT...
The Year in Review: Rethink Security
During a year of high-profile breaches like Equifax, HBO and Uber, as well as the realization that Yahoo’s highly-publicized 2013 breach compromised the accounts...
Nhash: petty pranks with big finances
According to our data, cryptocurrency miners are rapidly gaining in popularity. In an earlier publication we noted that cybercriminals were making use of social...
Travle aka PYLOT backdoor hits Russian-speaking targets
.travle-big-table td{border:1px solid #eee!important}.travle-big-table td{padding: 10px;}
At the end of September, Palo Alto released a report on Unit42 activity where they – among other things...
Jack of all trades
Nowadays, it’s all too easy to end up with malicious apps on your smartphone, even if you’re using the official Google Play app store....