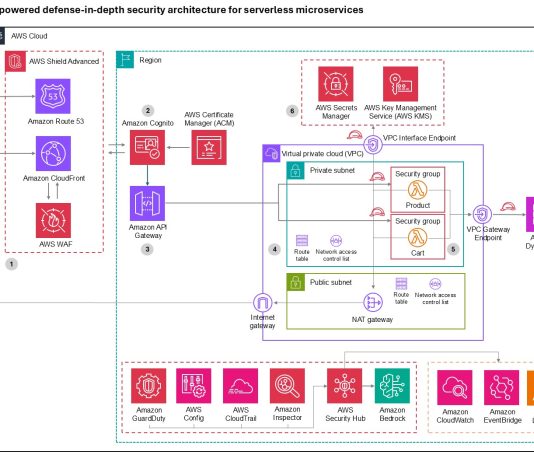
C-Suite Disconnect is Weakening Cybersecurity
Today, Centrify announced a new research study conducted with Dow Jones Customer Intelligence titled, “CEO Disconnect is Weakening Cybersecurity.” The report sheds light on...
A Slice of 2017 Sofacy Activity
Sofacy, also known as APT28, Fancy Bear, and Tsar Team, is a highly active and prolific APT. From their high volume 0day deployment to...
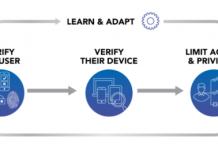
Break the Trust and Stop the Breach: The Zero Trust Security Model
As 2018 is upon us, it’s time to take stock of our new realities and commit to better behavior that benefits us and our...
Spam and phishing in 2017
Figures of the year
The share of spam in mail traffic came to 56.63%, down 1.68% against 2016.
The biggest source of spam remains the US...
Five Best Practices for Zero Trust Security
The Centrify Zero Trust Security model is effective because it allows organizations to remove trust from the equation entirely. Based on the assumption that...
RSA 2018
RSA 2018
Digital Guardian will be exhibiting at RSA 2018. Discover all the things happening at our booth and beyond!
...
A vulnerable driver: lesson almost learned
Recently, we started receiving suspicious events from our internal sandbox Exploit Checker plugin. Our heuristics for supervisor mode code execution in the user address...
Zero Trust Security for the New Australian Data Breach Law
Many Australian businesses need to rethink their approach to security to prepare for their nation’s new mandatory data breach notification law which take effect...
Gas is too expensive? Let’s make it cheap!
A few months ago, while undertaking unrelated research into online connected devices, we uncovered something surprising and realized almost immediately that we could be...
Escaping Data-Breach Groundhog Day
Countless companies globally are trapped in data breach Groundhog Day, unable to escape a repeating cycle of cyber attacks.
In the 2018 Thales Data Threat...