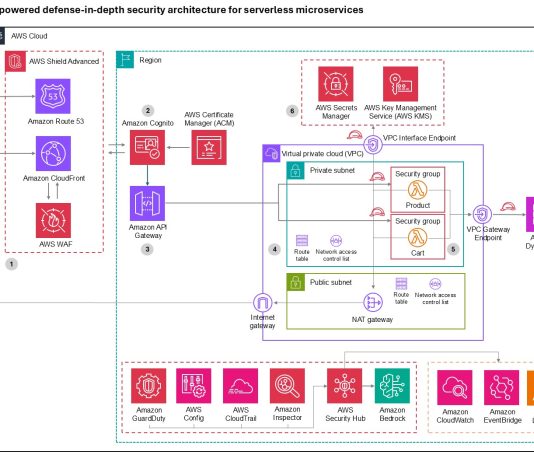
The Slingshot APT FAQ
While analysing an incident which involved a suspected keylogger, we identified a malicious library able to interact with a virtual file system, which is...
The devil’s in the Rich header
In our previous blog, we detailed our findings on the attack against the Pyeongchang 2018 Winter Olympics. For this investigation, our analysts were provided...
Frost & Sullivan Recognizes Centrify for IDaaS and PIM Leadership
Today Frost & Sullivan, a leading analyst firm and growth partnership company, announced that Centrify has earned the North American Product Leadership Award for...
With Less Than 100 Days to Go, How to Get C-Level Buy-in for GDPR...
For GDPR compliance initiatives to work effectively, there has to be buy-in from the boardroom. That doesn’t just mean releasing the necessary funds to...
Takeaways from the Russia-Linked US Senate Phishing Attacks
The Zero Trust Security approach could empower organizations and protect their customers in ways that go far beyond typical security concerns.
On January 12, 2018,...
Financial Cyberthreats in 2017
In 2017, we saw a number of changes to the world of financial threats and new actors emerging. As we have previously noted, fraud...
IoT hack: how to break a smart home… again
There can never be too many IoT gadgets – that’s what people usually think when buying yet another connected device with advanced functionality. From...
Multi-factor Authentication (MFA) Is Ready for Prime Time
We’ve heard it time and again. As security threats increase and morph, and user devices and locations diversify, multi-factor authentication (MFA) should be blossoming...
Subscribe to Data Insider
Subscribe to <span style="color: #11111; font-style: bold; letter-spacing: -1px;">DATA</span><span style="color: #E51892; font-style: italic; font-style: bold; letter-spacing: -1px;">INSIDER</span>
.blog_subscribe_block{ margin-top: 50px !important; margin-left: auto;...
Tax refund, or How to lose your remaining cash
Every year, vast numbers of people around the globe relish the delightful prospect of filling out tax returns, applying for tax refunds, etc. Given...